The General Data Protection Regulation (GDPR) is a Regulation of the European Union that protects natural persons (called data subjects) regarding the processing and free movement of their personal data. It was officially published in 2016 as “Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016” and became applicable on 25 May 2018.
The General Data Protection Regulation is a massive change in personal data protection with effects across the globe, designed for this information age with ever more big data, digitization and data-driven digital transformation and business in which data has become a key business asset and personal data is leveraged for ample business purposes. The GDPR is a massive change for several reasons, including the so-called extraterritorial applicability of the GDPR: its application expands beyond the borders of the EU and the EEA (European Economic Area).
The processing of personal data should be designed to serve mankind. The right to the protection of personal data is not an absolute right; it must be considered in relation to its function in society and be balanced against other fundamental rights, in accordance with the principle of proportionality (General Data Protection Regulation)
The EU GDPR also grants far more rights to data subjects and comes with more and further-reaching consequences for data controllers (who decide on the purpose and way of processing personal data) and data processors (who conduct processing activities on behalf of controllers).

The territorial scope of the General Data Protection Regulation (where it is applicable for types of personal data processing) and the expanded material scope have major implications on a global scale.
The impact of the General Data Protection Regulation (and the ePrivacy Regulation, lex specialis to the GDPR) gained widespread global attention in the wake of the Facebook and Cambridge Analytica data privacy scandal and significant personal data breaches at major companies.
Along with an increase in cyber risks and personal data protection legislation that has been adopted in several countries and regions, the GDPR and data protection regulations overall also led to an increasing attention for cyber resilience.
The General Data Protection Regulation in a nutshell: scope, compliance, fines, penalties and GDPR steps to take
A quick introduction on why the EU GDPR was deemed necessary and some essential aspects in a nutshell before embarking for a deeper dive, starting with the ‘what’ and ‘why’ of the General Data Protection Regulation. This chapter covers some essentials so please use the table of contents if the GDPR isn’t that new for you.
What is the meaning and definition of GDPR?
There is no real GDPR definition. GDPR is short for General Data Protection Regulation.
As mentioned, technically the General Data Protection Regulation text, as it is published in the journal on EU law and publications, is called “Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC”.
However, there are several definitions in the text of the General Data Protection Regulation for the terms it uses. If you are looking for GDPR definitions for terms beyond the scope of this GDPR overview, such as personal data processing, consent, controllers and so on, Chapter 1 of the GDPR text offers these definitions in Article 4.

Why did the EU replace the existing Data Protection Regulation with the General Data Protection Regulation?
The General Data Protection Regulation exists because of multiple reasons. A first one is that the mentioned Data Protection Directive or Directive 95/46/EC, although having been adapted, wasn’t fit to deal with the personal data challenges in these digital times anymore.
The EU’s Data Protection Directive already existed since 1995. In 1995 people hardly used the Internet. Although there have been additional rules since 1995, the EU felt it was time to replace the Data Protection Directive.
Early 2012 the European Commission said that the EU needed to be more in tune with the digital era in many perspectives, not just personal data. At the same time it also decided the time had come to reform the existing framework of data protection rules for that exact same reason. The Data Protection Directive was key in these existing data protection rules.
Examples of personal data processing include the storage of personal data, gathering and collecting personal data (regardless of means), aggregating, recording, exchanging, analyzing, publicizing, digitizing, enriching, structuring, changing, searching, leveraging, deleting, structuring, destroying, uploading and simply using/keeping personal data.
Moreover, the Data Protection Directive was a directive and the General Data Protection Regulation is a regulation. On 15 December 2015 the European Parliament, European Council and European Commission reached an agreement on the new data protection rules which would become known as the GDPR and replace the Data Protection Directive.
As a directive the predecessor of the EU GDPR was applied in quite different was by various countries. The EU wanted a far more consistent approach. The GDPR is designed for a single digital market in which organizations that are processing personal data know what they can do and what they can’t do with personal data. This way the digital economy, in which data are essential, should blossom in an increasingly data-intensive world. The GDPR offers the regulatory framework that is adapted to the reality of today’s digital world, while putting the data subject in the driver’s seat of his/her personal data.
Pretty much everything we do nowadays is driven by data and personal data are in virtually everything we do: using social media, buying online, opening a bank account, communicating via Skype, filling in forms on a website to receive promotions, getting loyalty cards from our favorite shops, visiting a physician, subscribing for a newsletter, interacting with governments, the list is endless.
Data controllers, have loads of data about natural persons which they process, store, collect, analyze and exchange. Although few companies have all our personal data, the aggregation of personal data can lead to very deep insights in our personal lives and privacy, with potential abuse as a consequence. The vast amount of personal data is also subject to potential breaches and personal data are often used in ways people have not explicitly agreed to.
In online advertising and social media, for example, a lot of pieces of personal data and so-called personal data identifiers are used to track and target us across many digital platforms and for purposes we haven’t given consent for or where another legal ground exists for the lawful processing of personal data, other than consent.
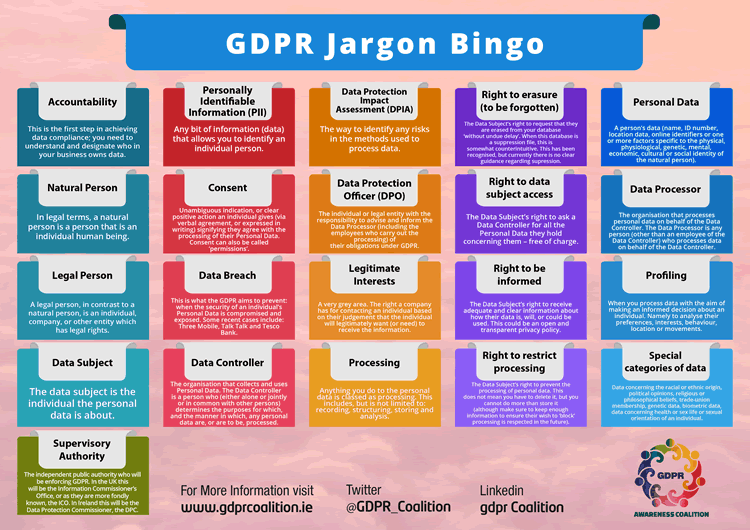
What is a data subject?
A data subject is an identified or identifiable natural person whose personal data need to be protected and get processed in the context of the GDPR.
An identified natural person is one that is singled out and as a natural person clearly identified without the need for further elements or identifiers. An identifiable natural person is not identified yet but can be identified. This can be done in relationship with additional identifiers such as a name and address.
The protection of personal data and the GDPR apply to identified and identifiable data subjects and to their personal data as well as all possible identifiers whereby some identifying data are considered very sensitive and are even more protected.
What is personal data and what is sensitive data?
Personal data means information that relates to a data subject, regardless of whether the data subject is identified in the scope data processing or can be identified.
Personal data include rather common data such as name, email address, place of birth, date of birth, a picture of the data subject and so forth.
Personal data also include other, less obvious data, including data and identifiers that are more typical to the digital economy. This can include an online identifier such as an IP address, location data, behavioral data acquired via modern means such as the Internet of Things (IoT) or facial recognition systems, cookies, RFID tags etc. but also data used in relationship with an organization or government such as an identification number.
Finally there is a category of personal data that is considered as sensitive data with additional protection needs and stipulations. These are personal data pertaining to, among others, personal health and health history, ethnicity, religious or political beliefs, social and cultural identity overall, genetic data and much more.
The GDPR also applies to pseudonymized personal data but not to anonymous data. Pseudonymization is a technique that is recommended by the GDPR.
What is a GDPR checklist?
A GDPR checklist is a list of things your organization needs to do in order to be GDPR compliant. However, there is no universally valid GDPR checklist which you can also see as a “GDPR to do” list.
As each organization is different, has different goals and activities, processes different types of personal data and has its’ own ways of working and own processes and challenges, a GDPR checklist is made in collaboration between the cross-departmental team that should make sure that all GDPR risks are listed, all GDPR protection mechanisms are in place and at all times the organization knows where personal data sits and how consent was obtained and the external consultants and advisors which are often needed to become GDPR compliant.
However, what is universal is that all GDPR checklists should include the steps to reach the before mentioned goals. It should include important duties such as GDPR staff awareness training and it also means you have an actionable plan and thus conducted your GDPR homework. Such a GDPR plan is the result of conducting a risk analysis, listing all the GDPR risks with regards to current personal data processing and protection practices against the backdrop of the organization’s duties in the scope of GDPR compliance, knowing what the issues to solve are, listing how they will be tackled and defining the priorities in the different tasks to complete on the GDPR checklist as you can’t do everything at the same time and some risks are higher than others and some types of personal data and data processing activities are more essential than others. Risk should be approached from the data subject risk perspective but you might also want to take into account the GDPR fines and penalties. Along with a GDPR awareness program and a GDPR action plan with a GDPR checklist or ‘to do’ list an organization demonstrates it has taken some steps in the direction of GDPR compliance which is essential.
What are the fines and penalties under the GDPR?
The GDPR stipulates GDPR fines up to 4 percent of the annual global turnover of an organization or up to 20 million Euros, with the additional stipulation that the highest of both is chosen in Article 83 of Chapter 8.
This does not mean that in case of non-compliance and/or personal data security breaches organizations will have to pay these staggering amounts. They are the maximum fines.
There have already been cases of very high fines in some EU countries with the GDPR in mind, before it actually became enforceable. While it is hard to predict what the GDPR fines and penalties will be in any given case, it is clear that as usual everything will depend on numerous factors such as the severity of the breach or not being compliant, the way in which data subject rights have been ignored or compromised, the level of non-compliance (with undoubtedly a look at what has been done on the level of staff awareness, risk assessments and steps to be as compliant as possible) and what has happened with the personal data.
If they are, for instance, internationally transferred without consent/authorization or access to them by data subjects is systematically refused or simply ignored, maximum GDPR fines are applied.
Although hard to predict the GDPR foresees clear fine mechanisms for various types of breaches and cases of not being GDPR compliant.
The GDPR, for example, doesn’t just stipulate maximum fines also foresees lower fines (10 million euros or two percent of turnover) for several other circumstances in which organizations fail to comply. These include not reporting data breaches in the ways the GDPR foresees or ignoring the privacy by design rules. More about the administrative fines in Article 83. Additional note: similar fines apply to the coming, previously mentioned EU ePrivacy Regulation.
On top of administrative fines, the General Data Protection Regulation offers multiple other penalties. If there is a suspicion that a company does not respect the data protection rules the appropriate data protection authority (DPA) can look into it and if there is a breach of the rules can 1) decide to impose a fine, 2) decide to take another measure (which could also be a reprimand or ban of data processing activity, for example) or 3) decide to impose a fine AND take another measure.
For more on the fines and penalties than offered in this GDPR overview, click the button below.
What do I need to know about GDPR compliance?
GDPR compliance simply means complying with all the rules of the General Data Protection Regulation regarding the personal data processing activities you conduct. Attaining it is less easy given the vast set of rules and many changes in the EU GDPR, compared to its predecessor, the Data Protection Directive 95/46/EC.
While the General Data Protection Regulation entered into force in 2016 the so-called GDPR deadline (the mentioned date it becomes applicable) is the time by when your organization should be compliant. This means that as of 25 May 2018 the mentioned high administrative fines of the GDPR also can be applied.
The General Data Protection Regulation foresees clear roles regarding roles and responsibilities within organizations to be able to respond to the requests of data subjects in exercising one of their many rights or the requests of controlling and monitoring instances.
The GDPR is not (just) about fines and deadlines. Compliance is an ongoing exercise. You need to have a strategic plan in place that starts with the major risks from the perspective of the data subject (and de facto you will of course also look at your risks) and the essential aspects of and changes in the General Data Protection Regulation, as stipulated in the GDPR text.
That text alone of course doesn’t answer all questions. That’s why there are data protection authorities, guidelines from DPAs and other authorities (which really do far more than giving fines) such as the European Data Protection Board and of course experts such as data protection officers (DPOs) which you might need to have to comply with the EU GDPR but which you also can hire if you strictly speaking don’t need to (DPO trainings are fully booked and soon there will be more DPOs for hire, e.g. in a DPO-as-a-service model that already exists) than you can imagine.
In other words: seek advice, not just in case of doubts. GDPR compliance is an end-to-end given and no legal text or guideline covers all. There will be cases where in the end a judge needs to rule as is always the case.
What matters is that road leading to compliance as an ongoing given that is all about risks and managing them. So, after having mapped these risks and essential tasks in a prioritized way you need to gradually move from tackling them to further compliance steps. The ability to demonstrate what you have done and still plan to do is key here, as is the ability to demonstrate compliance at all time, one of the duties of data controllers.
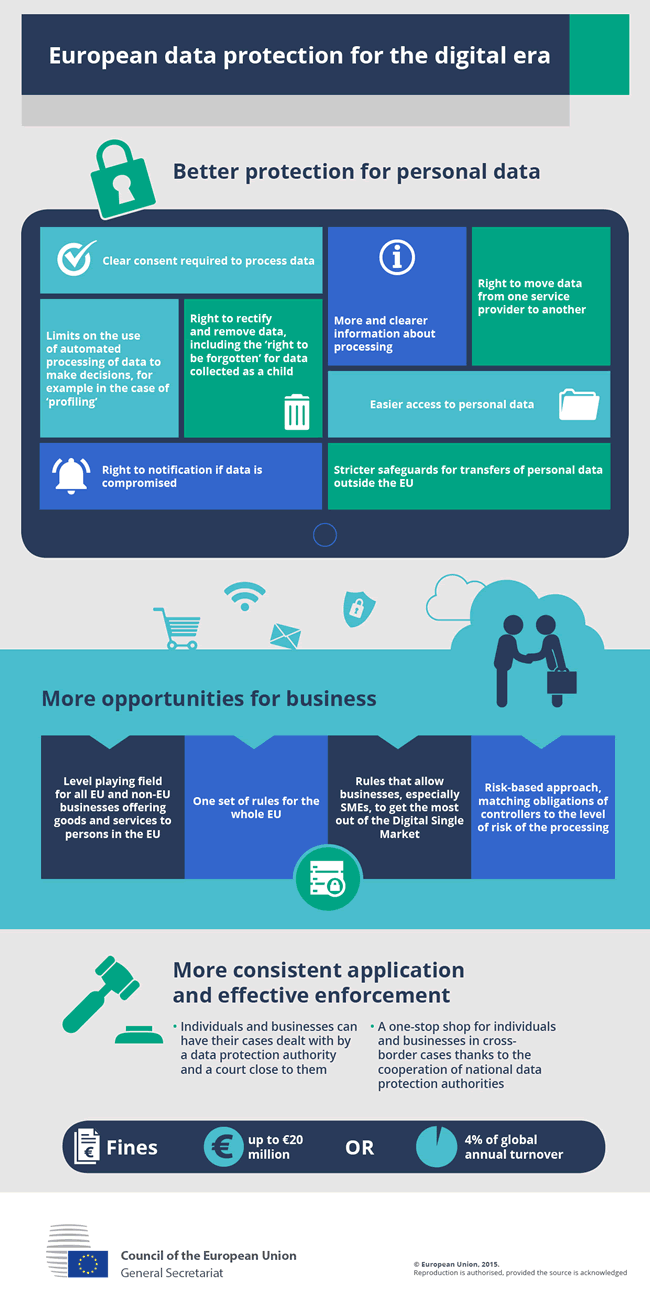
What should I know about the General Data Protection Regulation to be informed and get started?
Although the fines are not the best starting point, it’s key to ensure that the rights of data subjects can be exercised and that the appropriate legal grounds to lawfully process personal data are in place.
Not enabling data subjects to exercise their rights or ignoring their requests make it worse and can lead to higher fines when data subjects lodge a complaint which every single one of them can do and whereby the appropriate data protection authorities need to follow it up.
In other words: no reason for panic, yes reason to be careful, carry on and understand the essential changes in the GDPR, rights of data subjects, duties of controllers and processors, legal grounds for lawful processing, general data processing principles and stipulations concerning your individual business, various departments (HR, marketing, sales, customer service, anything), the types of personal data you process, appropriate security business measures and essential steps in an end-to-end way that starts with GDPR awareness and (awareness) training of your staff as people are the weakest link in data protection (both in the scope of information management aspects such as file sharing, using their tools for work etc.; and in the scope of cybersecurity) and making them aware (with policies to follow when dealing with personal data in the context of their work) is a first and easy step to demonstrate compliance. Other steps such as looking at the agreements with your data processors (when you’re a controller) and registering personal data processing activities with additional information on the what, why and how of the processing and the bases upon which the data was obtained are mentioned further in this GDPR overview.
Finally, note that GDPR compliance is also an ongoing exercise since data protection challenges evolve, jurisprudence evolves and so do the rules concerning compliance and new technologies and risks which pose challenges in a rapidly changing world.
In the context of technologies do take into account that the GDPR and its’ lex specialis, the ePrivacy Regulation, also cover personal data and PII (personally identifiable information) with identifiers in areas such as IoT (the Internet of Things, from wearables and smart home automation applications to personal data in so-called Industry 4.0 applications), the Internet, advanced ‘third platform‘ digital technologies and electronic communications, on top of many others. While the latter two are covered in previous laws as well they are broadened in order to be in line with the platforms and tools that exist today and there are of course quite a few of those (think social networks, applications like Skype, big data analytics, automated decision-making by attributing social scores in applications that rank people, often in combination with social activity and other data, e.g. ‘influence’, and so forth). IoT is new. So, here additional attention is required and ideally for applications in this space and in the context of new digital technologies a so-called data protection impact assessment is recommended. It’s indeed not just about cookies and email addresses anymore.
The GDPR: personal data protection and privacy rules for a thriving digital economy
As mentioned, fines and penalties are not the purpose of the General Data Protection Regulation. Moreover, it also fits in a larger context than the essential rights of consumers regarding (the usage and protection of) their personal data.
The GDPR is conceived as a framework for the protection of personal data and ownership of it in a digital transformation economy where data is a business asset, the new currency, the oil and an innovation accelerator; and where personal data is leveraged throughout connected ecosystems to achieve benefits thanks to a broader view of individuals in order to achieve better results across various disciplines.
In this economical, digital and societal context there are clear benefits for all organizations, yet there are also rules which need to be respected on the level of the individual without which a growing digital market is hindered by multiple challenges as we’ll see. In other words: as much as the GDPR might seem like a pain to many, it also is needed to make a digital and data-driven world easier and clearer. This offers benefits to organizations as well for several reasons we’ll tackle.
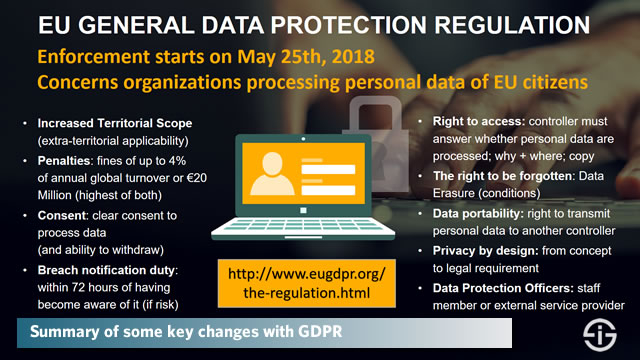
Key GDPR definitions, terms, rights and stipulations
To become GDPR compliant you don’t just need some tools. You need a thorough analysis, plan, detailed checklist and so forth, covering all aspects and processes involved. The first stage in any such strategy, checklist or compliance plan is awareness.
Although this is more about awareness and know-how of all stakeholders in the organization (including training your staff), we also need to understand some key terms, concepts, rights and duties in the GDPR. You probably have already most of this and there are far more exhaustive and detailed guides which you can see in the list below this overview.
The processing of personal data: the broad GDPR definition of processing
The GDPR is about the processing of personal data of natural persons in the EEA (which includes the EU), called ‘data subjects’ in the regulation.
‘Processing’ means any operation or set of operations which is performed on personal data or on sets of personal data (GDPR)
Processing covers a vast reality of actions and includes storage, dissemination, changes and management of personal data. Personal data also covers a broad reality of criteria, definitions, exceptions, personal data identifiers, pseudonymized data and more as we’ll see. Moreover, and this tends to be overlooked, it goes for the processing of personal data, whether the processing occurs with automated means or not. In other words: manually dealling with personal data (carriers) is included too.
In the second part of Article 4 (‘Definitions’) of Chapter 1 of the final GDPR text , the GDPR defines processing as follows:
‘processing’ means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction.
If you start thinking about who processes data of individuals, you start seeing the tip of the iceberg. The definition of processing is crystal clear and that indicates how the GDPR involves ALL activities regarding personal data. This also includes capturing, scanning and processing the personal data which hard copy documents contain and even the simple fact of “having” personal data (or we wouldn’t store or process them) or “having access to them”.
The GDPR definition and scope of the data subject and personal data
The EU GDPR definition of personal data leaves little room for interpretation too. In Article 4, the text states:
‘personal data’ means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural
person;
The GDPR definition is clear: if you deal with personal data of a data subject, the general rule is that the GDPR applies. However, there is a lot hiding under this seemingly simple definition as we’ll see.
On the other hand, there are several exceptions regarding personal data in areas such as public health and scientific research, so it’s important to understand the impact of the GDPR for your industry. This is again an argument to prepare in time and understand how it impacts your individual organization and activities.
Personal data which have undergone pseudonymisation, which could be attributed to a natural person by the use of additional information should be considered to be information on an identifiable natural person.
The EU GDPR does not cover anonymous data. However, it does cover so-called pseudonymized personal data because the pseudonymization, an often used ‘tactic’ in, among others security and analytics, can be reversed and, as opposed to anonymous data can be traced back to an identifiable natural person, the data subject. However, pseudonymization, along with encryption, is one of the methods the GDPR recommends as “an appropriate technical and organisational measures to ensure a level of security appropriate to the risk”.
Research indicates that quite some companies de facto use techniques to de-identify data as a way of reducing risk exposure.
Note that, in general, the more data are combined, the harder de-identification becomes and the higher the risks become. If special categories of data (“sensitive data”) are involved, additional risks and measures are the consequence.
Understanding the principles of data protection and information regarding identified and identifiable persons
Recital 26 of the GDPR is key for the understanding of the principles of data protection and stipulates that GDPR applies to any information regarding an identified or identifiable person.
It gives an essential overview of what kind of information regarding an identified or identifiable natural person the General Data Protection Regulation applies to. It also provides an overview of how it should be determined when a data subject or natural person becomes identifiable, states that pseudonymized data also fall under the GDPR and that anonymous information doesn’t. All these topics are further established in depth in more Recitals and Articles in the GDPR.
Online identifiers, genetic data and personal health data
In the GDPR the definition of personal data has been broadened (important for both consent and protection).
It includes identifiers such as genetic data and all data pertaining to a data subject’s health status. Also data for scientific research are included but only to a certain extent.
Genetic data include results from DNA analysis, health status data include data on treatments, medical history, diseases and far more – as the graphic below shows. Identifiers are data elements that could make a natural person identifiable and there are plenty of those. Some are more general, others are ‘sensitive’. It’s important to understand all these identifiers and how a natural person can become a data subject (the various ways in which he/she becomes identifiable). To give you an idea: one of the types of identifiers in the graphic below, namely online identifiers, consists of numerous sorts and forms, from an IP address and cookie to an RFID tag.
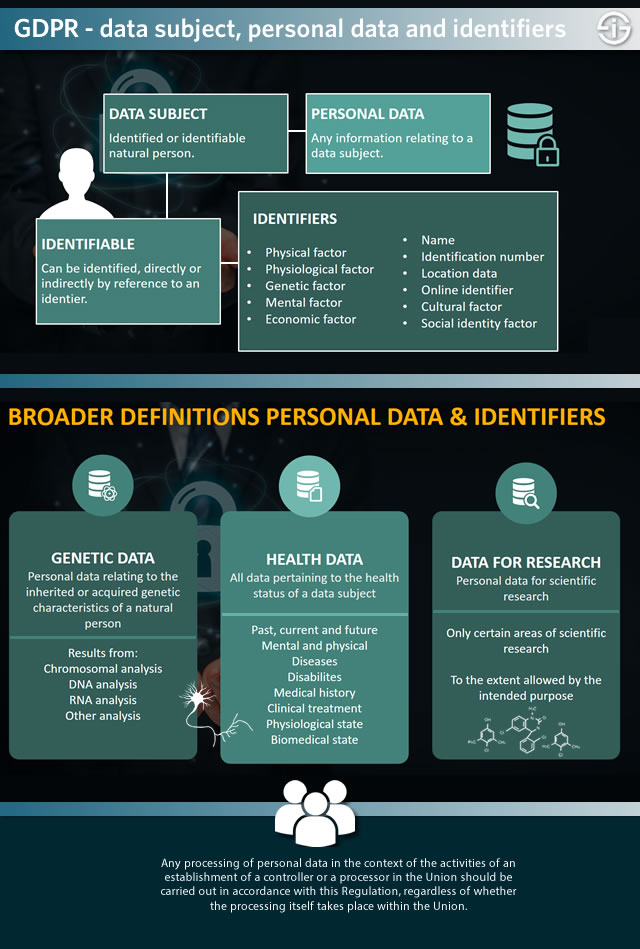
Recital 30 of the General Data Protection Regulation introduces online identifiers such as IP addresses, cookies, RFID tags and others, without being exhaustive. However, further in the text the GDPR zooms in on them.
The key thing to remember is that online identifiers such as the mentioned ones are considered as personal data because in combination with unique identifiers they can lead to the identification of a data subject and because such online identifiers, again in combination with other identifiers can and de facto are used for profiling, which is explicitly mentioned in the GDPR.
We see that many people do not know this and often even see surveys that indicate that professionals in various sectors do not consider other identifiers, such as even email addresses or photos as identifiers under the scope of GDPR. It is essential to understand they are (and in which context they are).
Genetic data are clearly considered as personal data as you can read in Recital 34. Moreover, genetic data are considered sensitive data and deserve special protection. The same goes for personal health data, which include information derived from genetic data but goes much further as is explained in Recital 35 of the GDPR that sums up various forms of healthcare-related personal data which fall under the GDPR (and for which there are special protection rules).
The expanded territorial scope of the GDPR
A major change of the GDPR, compared with the existing Directive, is its so-called extra-territorial applicability, the technical term for the mentioned fact that the GDPR doesn’t just affect EU companies.
The GDPR concerns all companies which process personal data of citizens (‘data subjects’) who reside in the EU, regardless of where these companies (the ‘data processors’ and ‘data controllers’) are located.
When the processing of personal data of EU data subjects is done by a controller or processor that is not present in the EU, the GDPR applies in activities related to offering goods or services to EU citizens (free and paying services) and behavior monitoring of EU data subjects.
Moreover, a non-EU company which processes the data of EU citizens needs to appoint a representative in the EU.
Relevant links and texts regarding this territorial scope include:
- GDPR Recital 22 which says that any processing of personal data in the context of the activities of an establishment of a controller or a processor in the EU should be carried out in accordance with the General Data Protection Regulation, whether the processing happens within the EU or not.
- Recital 23 of the GDPR text which essentially stipulates that the processing of personal data of data subjects in the EU with regards to the offering of goods and services (with or without payment) by organizations outside of the EU is subject to the GDPR.
- Recital 24, which says that the GDPR applies to organizations that are not in the EU but monitor behavior of data subjects in the EU.
- Recital 25, which covers the territorial application of the GDPR in the scope of public international law, with for instance diplomatic missions outside of the EU, where EU rules apply, falling under GDPR.
- Article 3 (‘Territorial Scope’) of the General Data Protection Regulation which summarizes it all and specifically tackles that territorial scope of the GDPR.
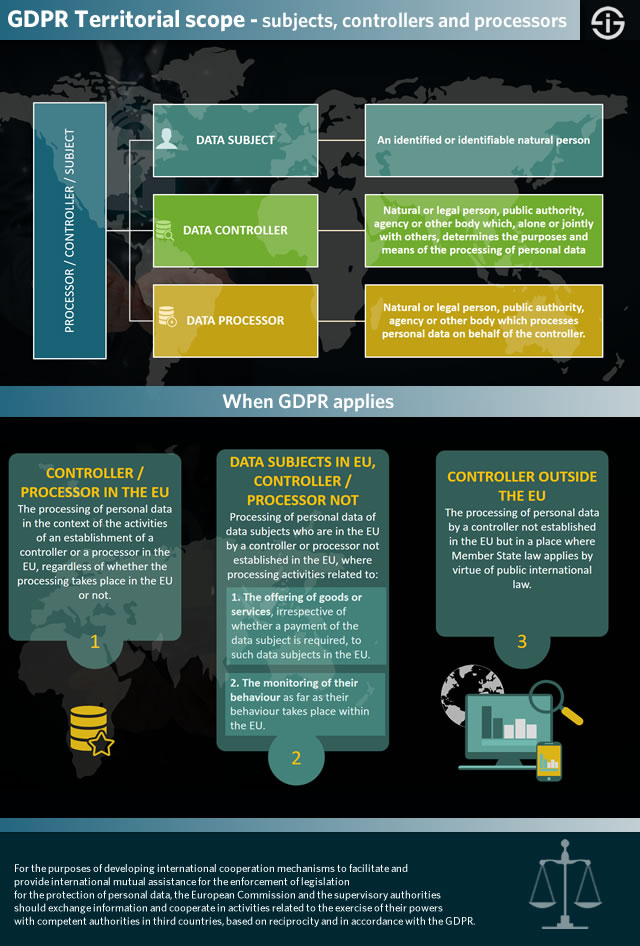
GDPR and the duties of controllers and processors
The GDPR hasn’t changed the definition of controllers and processors that much in comparison with its predecessor. What has changed though is the impact with regards to processors (and the flows of reporting and obligations in the overall picture of various players with on top of the controllers themselves also the role of the supervisory authorities and the European Data Protection Board which replaces the Article 29 Working Party as mentioned further in this GDPR compliance guide).
In the infographic on the territorial scope of the GDPR we already mentioned the definitions of the data controller and the data processor.
- The data controller is any natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data. Let’s say it’s the main organization.
- The data processor is the natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller. So, depending on the type of personal data processing activity, it’s really everyone that takes care about specific processing tasks as an outsourcing partner for any possible business function involving personal data as processing is so broadly defined as mentioned elsewhere.
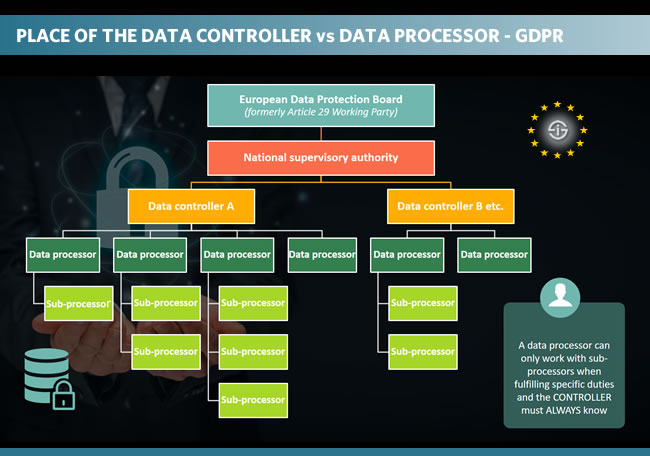
We dedicated a special page to the role of the data processor as data processor obligations are numerous under the GDPR and there is a de facto shared liability in case of infringements or personal data breaches.
Processors must follow the exact same principles of personal data processing as controllers do. On top of that, processors, among others,
- Must keep a record of all processing activities they have done for a controller (audit trail) and of all controllers they conduct data processing activities for,
- Must have a contract or legal basis that clearly describes what they do for the data controller, for how long, for which reasons, which types of data and categories of data subjects and more,
- Must assist controllers in many obligations such as secure data processing, the notification duty in case of a personal data breach (with a personal data breach notification duty from processor to controller), the potential need for a data protection impact assessment or prior consultation,
- Must inform the data controller when using or considering to use the services of other data processors with the additional obligation to have a clear mandate for the described personal data processing activities.
In other words: the GDPR is highly impactful for data processors and thus all sorts of outsourcing companies in areas such as marketing, data services, human resources, logistics, you name it.
The list of processor obligations above is far from complete. They must work in secure and compliant ways themselves, they must operate in far more transparent ways with the data controller than before, the data controller in turn must be far more attentive to the degree of compliance of processors he works with, there must be a clear data processing agreement and processors are liable in more (direct) ways than before.
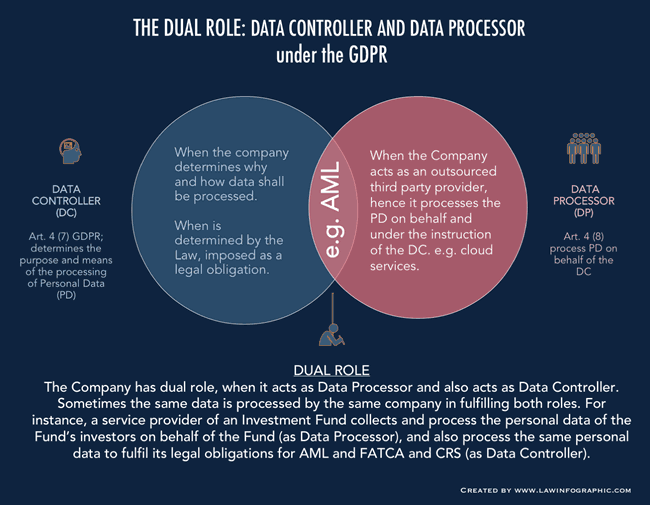
Note: in some cases an organization can act both as a data processor and data controller at the same time. Jessica Lam explains when that is the case in the infographic below and in the full article on the topic.
GDPR compliance and consent: consent definition, importance and rules
The GDPR is stricter with regards to consent than its predecessor. Consent remains one of several legal bases for the lawful processing of personal data. However, when it is chosen as the legal ground it adds upon the general data subject rights which we cover further in this GDPR compliance guide and whereby attaining GDPR compliance means being able to meet the requests of data subject rights when they want to exercise such a right.
Consent should be given by a clear affirmative act establishing a freely given, specific, informed and unambiguous indication of the data subject’s agreement to the processing of personal data relating to him or her, such as by a written statement, including by electronic means, or an oral statement.
With consent as a legal ground, additional rules apply and the degree of control of the data subject over his/her personal data is greater, while the duties of controllers and processors increase and additional, specific consent-related rights join general data subject rights such as the right to withdraw consent. In practice this is difficult and needs a consent management possibility. So, at all times it is key to see what is the best legal basis as consent is certainly not a holy grail nor a walk in the park. However, in several cases it will be the most appropriate legal ground or perhaps the only (valid) one for specific personal data processing activities.
Under the GDPR, when consent is chosen as the lawful processing basis in any data processing activity, consent needs to be proven by the data controller. Consent also needs to be freely given, specific, informed, unambiguous and given by a statement or clear affirmative action. All these elements are crucial.
By choosing an action-based consent approach GDPR compliance doesn’t just mean a harder duty to prove consent when it’s chose, it also means that the way in which consent is gained needs to be really based on a data subject’s clear action instead of being gained through pre-ticked boxes, inactivity, silence and several other grounds which might make it harder for the data subject to freely consent. The other mentioned elements regarding consent are obviously related with this notion of active consent whereby freely given, specific, informed and unambiguous de facto are intertwined.
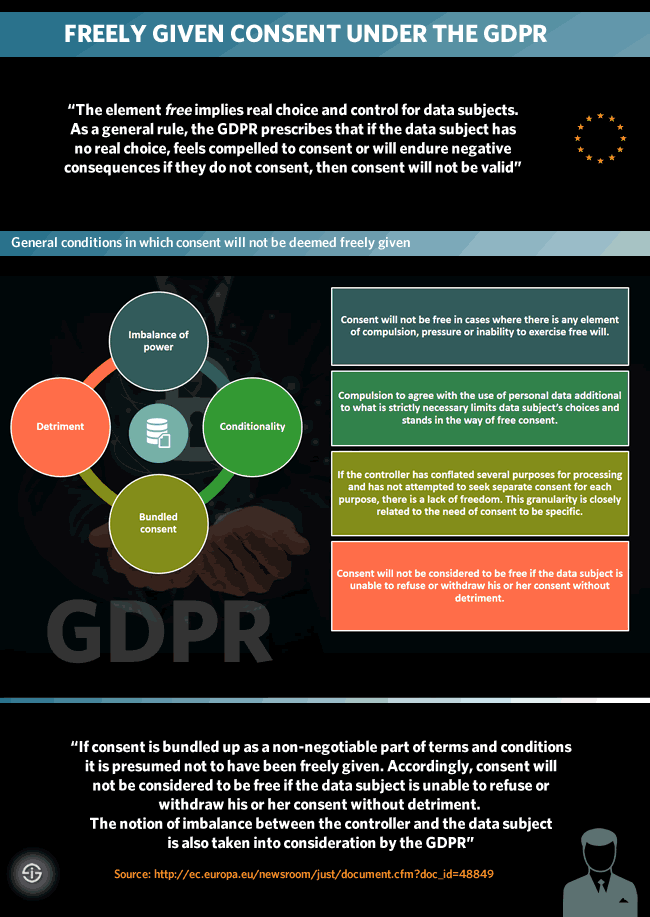
If consent for a data processing activity is bundled with other terms and conditions to use services or with contracts, without the consent for the specific data processing activity being separated from these terms then consent is deemed not freely given as consent needs to be given for each single activity (granularity).
Moreover, data controllers must use clear and simple language about the purpose of the processing activity for which consent is sought and consent needs to imply a real affirmative and free choice whereby there are several notions which make freely given consent invalid.
An example of this: when consent is given in a context where there is a clear imbalance of power between data controller and data subject, consent will not be considered as being freely given.
There are also limits on the use of some forms of data processing whereby explicit consent is needed, an even stricter form of consent that strictly speaking only applies in some conditions.
As said, consent regarding the processing of personal data needs to be crystal clear and in plain language.
In practice this means gone with the legalese and easily distinguishable and accessible ways of describing for what consent is given and how it is given by the data subject. That same level of easy must apply to the withdrawal of consent. Moreover, personal data can’t be shared with other parties, without consent.
Consent and consequences/duties regarding consent in detail
GDPR Recitals and Articles determine how consent should be given, when it applies and when not, what the duties of organizations are regarding consent, how the data subject can withdraw consent and far more.
It all starts in Recital 30 of the GDPR where it is clearly mentioned that consent regarding the data subject’s agreement to the processing of his/her personal data must happen by a ‘clear affirmative act’, as just mentioned. It must not just be clear and affirmative, it must also be a freely given, specific, informed and unambiguous indication of that agreement.
All this has even more consequences.
- Freely given means that in no way there has been compulsion, pressure or inability to exercise free will. Freely given consent also means that consent, when used as a legal basis for lawful processing of personal data, can be freely (and easily) withdrawn at any given time by the data subject with no negative consequences or detriment whatsoever.
- Informed means that the data subject does know what he/she is agreeing to, which is a duty of anyone asking consent.
- Clear means that organizations can’t hide the agreeing to personal data processing, as well as the purpose of it and the rights of the data subject, in legalese or ambiguous ways.
- Specific means that consent is given for the specific purpose and in the specific scope of the reasons why consent is asked, how personal data will be used and so forth.
- An affirmative act is what we mentioned previously regarding the dimension of activity from the data subject’s side whereby, among others, pre-ticked boxes are a ‘no go’.
In other words: it stretches far and really puts the informed data subject at the center. Recital 32 clearly means end of pre-ticked boxes in consent as these do not mean consent. Clarity and transparency is key. Transparency is further tackled in the scope of the rights of the data subject in Chapter 3 of the GDPR text (mainly Section 1).
There are many Recitals and Articles covering consent so do check the rules for your specific situation. By way of an example: Recital 33 of the GDPR looks at consent and personal data in the scope of scientific research.
In, among others, Chapter 2 of the GDPR text (Articles 5-11) the topic of consent is tackled in more details, including the conditions for consent, consent and children below the age of 16, the right to withdraw consent and more.
The difference between explicit consent and specific/unambiguous
There are often misunderstandings with regards to the meaning of explicit consent. Explicit consent is not mentioned in the definition of consent as it is stated above.
A two stage verification method is recommended as a good option in the case of explicit consent.
However, the term explicit consent comes back a few times in the GDPR, among others in Article 9 about special data categories, GDPR Article 22 on automated decision-making and profiling and in GDPR Article 49 on derogations in international data transfers.
In December 2017 GDPR consent guidelines from the Article 29 Data Protection Working Party, explicit consent is one of several consent-related topics which are mentioned.
Explicit consent is needed in specific circumstances where there are serious risks to personal data protection and an even higher level of individual control over personal data is considered appropriate.
In other words: explicit consent is not the same as specific consent nor any of the other terms used in the GDPR’s consent definition. The mentioned guidelines elaborate further on mechanisms to obtain explicit consent and in which cases you need it as you can read in our article.
GDPR compliance and the legal bases for lawfully processing personal data
Consent is just one, albeit the most often mentioned, legal basis for lawful processing. This in no way means that consent is more important in the eyes of the GDPR, even if the rules are stricter.
We keep saying it: having the most appropriate legal basis for personal data processing activities is what matters. On top of consent, the other legal grounds for lawful processing of personal data are depicted below. They are contractual necessity, legal obligations, vital interests, public interest and legitimate interests.
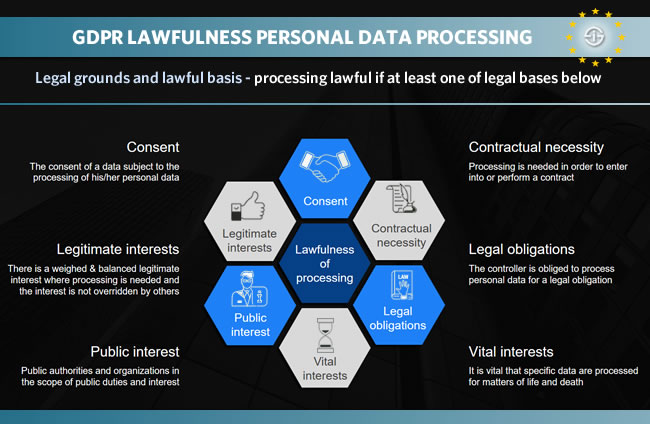
A quick look at each of them except consent which we just covered. Moreover, for consent, explicit consent, the legal grounds for lawful processing and so forth there are more articles we point to in this GDPR compliance guide.
Contractual necessity
Contractual necessity, as the name implies, is indeed a legal ground for lawful processing where the performance or steps to take in order to enter in a contract require the processing of specific personal data.
It’s clear that in several types of contracts it’s pretty hard to have one in place if you don’t know with whom you have a contract. Gaining the essential data to make the contract happen is a form of processing and as these data are personal data, the GDPR applies.
This isn’t new and existed in the predecessor of the GDPR so it won’t affect existing contracts too much. However, do make sure that the personal data you ask in order to enter in a contract are needed for the contract (don’t go beyond the strictly needed data in the scope of the contract), check all data processing activities you conduct in the scope of contracts, check for examples of contracts in specific business functions (e.g. HR) or industries, get help in case of doubt and make sure you don’t mix several purposes and legal bases in one contract if one of them is consent. Do also check out the GDPR Articles and the GDPR Recitals for specific industries, business activities, data processing activities and stipulations regarding contracts.
Legal obligations
Legal obligations, also as the name implies, means that in order to fulfil their legal duties data controllers simply have to process certain personal data.
This already existed as a legal ground, just like legal obligations. However, the GDPR limits legal obligations to those in the scope of laws of the EU or EU Member States.
While this isn’t new and you should already have this in place, once more check for compliance with the GDPR, list the various data processing activities in the scope of legal obligations, see when it plays as a legal ground and do look for your industry. Moreover, the limitation to the laws of the EU and its Member States does come with consequences.
Vital interests
Vital interests in essence is when you need to acquire some personal data in order to help a natural person and don’t have time to even think about rules and regulations.
In other words: essentially matters of life or death or of potential disasters for people when you don’t act as in immediately. Examples could be when you need urgent information from people who have just been in an accident and in the process of trying to help them that information is simply vital. Moreover, in cases where it’s really a matter of life or death and literally of vital interests, some of these data can serve public interest. Really do think disasters here.
Public interest
Public interest is mainly a legal basis in the context of the tasks and duties of public authorities and the duties controllers have in the public interest or towards public authorities and the public interest.
Public interest isn’t new either so to most it will already be known and it does exist in non-EU data privacy laws as well. Scientific research and public health are some of the activities that come in the picture here.
Legitimate interests
Legitimate interests is one of the most mentioned alternative for consent in several circumstances. It isn’t new in the GDPR but you need to be very careful when considering to do so as there are exceptions and tiny little details that are easy to overlook.
An example of a legitimate interest is when there is a relevant and appropriate relationship between the data subject and the controller in situations such as where the data subject is a client or in the service of the controller. Legitimate interests are often used as alternatives for consent in the scope of marketing where there is also the question whether the GDPR means that you need to reconsent; meaning: ask customers to consent again. In general you don’t if you already worked according to the rules of the predecessor of the GDPR. The devil, however, is in the details: this only goes if what you did before was in line with the GDPR. So, check twice.
Other examples of legitimate interests such as network and information security reasons, and more on each of these legal grounds via the button below.
Processing personal data: principles of transparency, lawfulness, fairness and more
On top of the legal grounds to lawfully process data there are the general principles of transparency, fairness and lawfulness in personal data processing.
So, do check out Article 5 and Recital 39 of the General Data Protection Regulation as it covers the essence of transparency, lawfulness and fairness in the processing of personal data under the GDPR and several consequences for organizations processing these data.
The Recital and Article go more into detail with regards to transparency (e.g. why the personal data will be processed, the obligation to make it easy to find and understand for the data subject, the obligation to use clear and plain language) but also looks at the essential rules regarding the limitation in time of personal data store and fundamental obligations to ensure that data subjects can exercise the several rights they have under the GDPR (principles of transparency, purpose limitation, storage limitation etc.).

Consent of the data subject and in several cases other legal grounds are the basis of the lawful processing of personal data under the GDPR and, as a general rule (with the usual exceptions) it is up to the organization (or the controller) to be able to demonstrate that the data subject did give consent for the processing of his/her personal data or that there is another basis for lawful processing. It is also up to the controller to make sure that compliance with the several data processing principles occurs and is demonstrated. (the principle of accountability).
Personal data breach notification duty
The GDPR has clear rules on when and how to report personal data breaches that pose a risk to data subjects. GDPR compliance means being able to meet that duty.
The breach notification duty implies several things. First it means that personal data breaches need to be communicated to the so-called supervisory authority. This personal data breach notification should happen within undue delay and not later than 72 hours after the controller is aware of it, if feasible.
If it takes the controller longer than 72 hours to submit a personal data breach notification, the notification needs to be accompanied by an explanation of the reasons for the delay.
If the personal data breach is unlikely to result in a risk to the various rights and freedoms (which are interpreted broader than those in the GDPR alone), all this doesn’t apply.
A personal data breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed (GDPR Article 4, Definitions)
In case of a personal data breach with the likely risks for the data subject the processor obviously also needs to notify the controller. However, that must happen without undue delay after becoming aware of the personal data breach. This is explained in GDPR Article 33 where there are also rules about what the personal data breach notification at the least should contain.
On top of the duty of the processor to notify the controller and the controller to notify the supervisory authority when the personal data breach is likely to lead to a high risk to the data subject’s rights and freedoms, the controller must also communicate the personal data breach to the data subject, here again without undue delay.
The essential rules regarding this communication of a personal data breach to the data subject and the cases in which it isn’t required are in GDPR Article 34.
GDPR Article 4, which contains the GDPR definitions, defines what a personal data breach means as you can read in the quote.
The special protection of personal data of children
The specific protection of children in the scope of their personal data is established in Recital 38 of the General Data Protection Regulation.
Here, the role of the parent and general rules regarding personal data protection of children are mentioned, mainly in the scope of marketing, profiling and gathering personal data of children for services which target them.
The precise details are further established in the text. In Article 8 (Chapter 2 of the GDPR text) the age of 16 years is introduced although EU Member States can foresee laws for lower ages in specific conditions whereby that lower age can never be below the age of 13 years.
The special protection of children is so essential in the scope of the GDPR that it should absolutely rank high on your GDPR compliance list.
GDPR compliance and the Data Protection Officer
A Data Protection Officer or DPO in the scope of the GDPR is only needed in case an organization is a public authority (with an exception), has personal data processing activities on a large scale whereby the main scope is to observe data subjects and in organizations processing data of specific categories of data at scale.
A Data Protection Officer has clearly defined duties and needs to be experienced on the level of data protection law and practices and needs to be able to work in an entirely independent way. However, there isn’t an exact ‘job description’ nor a fixed set of rules with regards to the past experience of a DPO. A Data Protection Officer can be appointed and selected in many ways: he or she can be internal to the organization (internal only if there are no conflicts of interests and issues with regards to the ability to work independently) and can even be ‘shared’ by several organizations.
For the exact duties and role, as well as the skillset of the Data Protection Officer click the button below where you find far more than in this GDPR overview. The infographic summarizes when a Data Protection Officer is required by the GDPR.

Data subject rights and GDPR compliance
The GDPR takes over several data subject rights from its predecessor, the Data Protection Directive. However, on top of expanding and tightening the rules regarding some data subject rights, the General Data Protection Regulation also introduces new data subject rights. We tackle several of them in depth across our site. Below are some.
It’s clear that GDPR compliance means that you have done everything what you could to enable data subjects to exercise these data subject rights. And that’s not even enough. GDPR compliance also means that you have properly informed data subjects in a transparent and clear way about those rights.
Data subject rights: the right of access and to information
The right to access is also a right of information, transparency and also of (withdrawal) of consent.
Data subjects can ask the data controller whether personal data concerning them are processed or not, why, where and how this is done, and get an electronic copy.
Data subject rights: the right to be forgotten or data erasure
Data subjects can ask data controllers to erase their personal data. Moreover, if a clear consent exists to disseminate the data and/or third parties process the data, this consent can be withdrawn. However, there are conditions that apply.
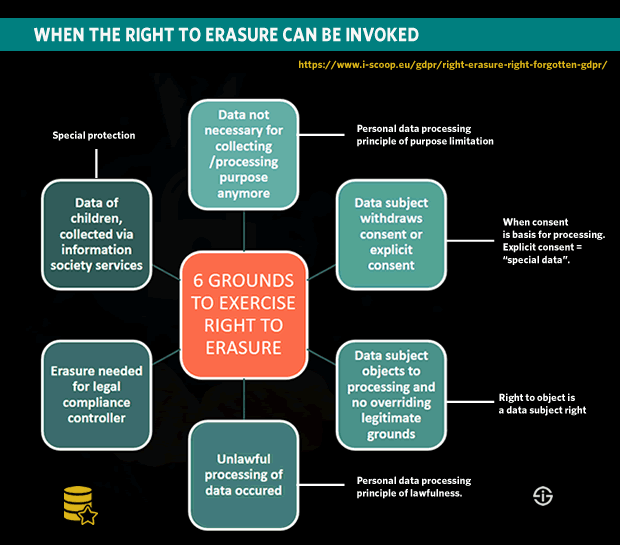
A closer look at the right to data erasure or right to be forgotten. Data subjects have the right to ask erasure of personal data regarding him or her in specific conditions.
The grounds on which that right to be forgotten can be invoked (and whereby the controller must erase the data without undue delay and also report on it) are:
- The fact that the personal data are no longer needed in relationship to the purpose for which they were gathered or processed,
- The withdrawal of consent in case consent is chosen as the basis for lawful processing (or explicit consent in the case of special categories of data) with the additional stipulation that there is no other legal ground for processing besides consent,
- The data subject objects to the processing (with the right to object being another data subject right) as is stipulated in the first paragraph of GDPR Article 21 with the general rules on that right to object or where the personal data are processed for direct marketing (including profiling in the scope of direct marketing),
- The personal data which are asked to be erased have been processed in an unlawful way to begin with,
- There is a legal obligation the controller is subject to and that requires the erasure in order to be compliant with that legal obligation,
- The personal data concern children and have been collected to offer information society services directly to a child as is mentioned in paragraph 1 of Article 8 of the GDPR.
Additionally, if the personal data which are asked to erase have been made public one way or the other by the controller (e.g. putting personal data on the Internet where others can consult them), the controller must try to make sure that links to that data, copies and replications are removed too.
However, this is not absolute: it must take into account the technology that exists to do so and the cost of implementing it and the efforts of the controller must be ‘reasonable steps, including technical measures’.
Exceptions to the right to be forgotten or right to erasure include following reasons for which processing (in proportion) is needed:
- The exercise of the right of freedom of expression and information,
- Processing activities to meet a legal obligation,
- Reasons in the scope of public health,
- Purposes of archiving in the public interest, purposes of scientific or historical research, and statistical purposes,
- The establishment, exercise or defence of legal claims.
The full text – with links – regarding the right to erasure or right to be forgotten in GDPR Article 17.
Data subject rights: the right to data portability
The right to data portability is a new concept that comes with the GDPR. In a nutshell: data subjects have a right to receive personal data about them (as mentioned) under specific conditions but on top of that also have a right to transmit it to another data controller; this only goes when data processing is done using automated means.
The right to data portability gives the data subject a right to receive personal data concerning him or her in a structured, commonly used and machine-readable format, as well as the right to transmit those data to another organization. It’s a data subject right for digital data and the digital age.
- It is the duty of the controller to make this possible so the data subject can transmit his personal data to another controller.
- It is also the duty of the controller to make this possible without any hindrance.
- If it is technically possible, a data subject should also be able to directly transmit those data from controller A to controller B. In other words: without the need of the controller to intervene but, again, only when technically feasible.
The right to data portability implies that:
- either the processing happens because the data subject has given consent (and thus consent is used as a basis or lawful processing) or, if it concerns special categories of personal data, the data subject has given explicit consent;
- either the processing is needed for the performance of a contract where the data subject is a party (a second basis for lawful processing);
- the processing is done using automated means (so, digital and electronic).
We already mentioned other key aspects such as the higher fines (penalties) and the adoption of the privacy by design principle.
Other key elements and/or changes in the GDPR
The list above is far from exhaustive. In the resources, infographics and other material in this article you find plenty more changes and elements.
In order to be able to demonstrate compliance with this Regulation, the controller should adopt internal policies and implement measures which meet in particular the principles of data protection by design and data protection by default (GDPR)
These, among others, include:
- Privacy by design and data protection by default are two key principles which have an impact on many areas as we’ll see. As an example, privacy by design plays on the level of records management.
- The so-called one-stop shop which means that international organizations de facto have to work with one supervisory data protection authority.
- Flexibility regarding specific articles. As opposed to popular belief, there are several areas where national regulators can interpret and/or elaborate on stipulations in the GDPR. This is among others the case in the context of sensitive data.
- International data transfer principles are part of the GDPR.
- Organizations need be able to demonstrate that adequate technical and organizational measures have been taken. Certifications such as ISO 27001 can help in demonstrating this.
- Lawful processing: as said, consent is put forward in the GDPR; however there are more elements that matter in the broader context of lawful processing.
- Specific measures to decrease risk, with encryption being the main one, are ‘promoted’ by the GDPR. As said, also rendering data pseudonymous is a way to decrease risk.
- New rules regarding DPIA’s: there are several cases in which a Data Protection Impact Assessment is mandatory, again with a focus on ‘new technologies’.
GDPR compliance strategies and GDPR checklists
Optimization, (restoring) trust, a more holistic approach and turning security and information better into the enablers of digital transformation are just a few benefits that smart organizations can achieve with frameworks such as the GDPR (you’ll find more below).
On the other hand, there is the hard work that is needed in order to become GDPR compliant. As said, strategic approaches, looking at all aspects of the business, are key.
Various organizations, often in a collaboration with others which have subject matter expertise in one or more specifc areas of the practical implications of the GDPR have come up with such strategic approaches. As a matter of fact, this is also part of the whole GDPR reality. The GDPR foresees Data Protection Impact Assessments.
They all, more or less, have the same steps in common, and are part of any GDPR compliance checklist or data protection and risk detection checklist.
GDPR compliance step 1: EU GDPR awareness
Obviously organizations need to be aware of the GDPR and its implications. That’s part of what we do in this overview and, as mentioned, there are quite some organizations that lack awareness and/or won’t be ready.
However, in the strategic approach to GDPR compliance, awareness means something else (too): your staff, management, IT team, security people, information managers and so forth also need to be aware of what the GDPR in practice means for them. This is typically done in workshops and trainings to move from being aware to acting aware, from understanding to acting accordingly.
Note that it’s important to have people that are responsible for creating this awareness and that education will be a recurring theme as new people join the company. The GDPR also foresees several roles.
The GDPR also shouldn’t be seen as a single big effort to be ‘ready’ by May 25th, 2018 of course. Data protection, in the scope of the GDPR and beyond, requires an ongoing effort, evaluation, monitoring and controlling. Moreover, it’s not as if tomorrow you won’t be leveraging new technologies with, again, new questions.
Finally, awareness also means fully understanding the GDPR and its impact, otherwise it’s hard to see where the gaps are between where you stand now and where you need to be of course.
GDPR compliance step 2: GDPR assessment/audit: discovery and gap analysis
These gaps bring us to a second part in all strategic approaches: there is a stage of assessment/audit with discovery and gap analysis. In order to get somewhere you need to know where you stand today, it’s a universal given.
And to assess where you stand today – and thus also look at the gaps – this stage is one of discovery and mapping pretty much anything that is relevant in the scope of the GDPR.
So, you need to gain insights in your current practices on various levels such as audit capabilities/methods, where data sits (data discovery), which processes are involved, how you process data, how your privacy and security practices function, who is responsible and accountable today, what kinds of systems, networks and databases come into the equation and so on.
When conducting a risk assessment, look at the risks for individuals’ rights and privacy.
In practice, assessment/audit and awareness, as you can imagine overlap somewhat. Seeing what you do can lead to awareness regarding aspects you might have overlooked and vice versa.
In practice, an assessment and discovery stage also needs to lead to an analysis of the gaps. As said, this obviously also means that you already know the GDPR and its full impact as a sort of benchmark that guides you in assessing in a prioritized way with the gaps in mind.
An audit further includes a gathering and analysis of all current document policies in the organization as they exist now: from security and business continuity policies to acceptable use and privacy policies.
Some additional GDPR audit tips:
- Audit to map risk. It is adviced to take all elements of risk and classify them from a prioritization perspective. When conducting a risk assessment, don’t (just) think about your organization’s risks. The GDPR wants you to look at the risks for individuals’ rights and privacy.
- Assess all frameworks, organizational aspects, strategies and security/data/incident/reporting management practices.
- Focus on people: it’s not just about the risks in current practices, processes, systems and frameworks, it’s also about organizational culture towards personal data protection and skillsets.
- Get the documents. Make sure you have access to all other data and documents which contain information on your latest security assessments and incidents and so on.
- Listen. As we all know there is often a world of difference between documented policies and real-life practice. This inevitably means that you need to talk with people about how they work in practice, regardless of any documents and policies.
GDPR compliance step 3: Planning/strategy – preparing the GDPR actions to be taken
Once you know where the gaps are it’s time to get really strategic and planning what needs to be done to close the gaps and taking all the other measures which you’ve identified.
The goal of a plan is to execute it and requires a full picture of the gaps, various involved areas and roles and responsibilities.
As the GDPR touches upon so many areas you will essentially need to plan in an integrated and holistic way too. Planning and, next, acting in a holistic way is one of those benefits you can achieve as you go to a GDPR compliance exercise. After all, digital transformation, security, information management, marketing, customer service and so forth need a holistic view to succeed as well. And we do still live in a reality with many silos.
In practice, you’ll plan across several functional and practical areas, however. These include:
- Information management and governance
- Security (and ICT as security needs to be guaranteed everywhere)
- Human resources
- Legal
- Marketing, management of online presences and advertising (note that the GDPR will be complemented by a new EU ePrivacy Regulation).
- Customer service and contact center
- Etc.
You will also have to look at the ecosystem of your business, with among others third-party data partners and business process outsourcers (BPOs) and thus at SLAs too (vendor management and third-party risk management).
In the planning stage (and also in the audit stage) you’ll have to look at, among others:
- The practical aspects of moving to a ‘privacy by design’ organization.
- “New” information governance plans.
- Implementation plans regarding information management, security and privacy initiatives.
- Plans regarding access policies, role management and the security controls which need to be put in place.
- Plans to solve the potential vulnerabilities you detected in the assessment/audit stage.
- Policy plans for the mobile workforce and action plans to tackle shadow IT.
- Plans regarding audits and roles and responsibilities (e.g. the Data Protection Officer).
- Plans regarding the roll-out of technologies that help improve security and privacy.
- The plans regarding information audits, data retention, Master Data Management (MDM), device management (mobile phones of workers,…), etc…
- Very specific plans in the many very specific aspects of security and technology: GDPR and cloud, GDPR and IoT, the list goes on.
GDPR compliance step 4: Taking action: doing what you’ve planned
Have a plan? Time to get practical, roll it out and deploy across all the areas you’ve identified and planned for.
As promised below we dive a bit deeper into two areas with links to additional resources which tackle various implications and actions to take in these areas.
However, as mentioned the various components need to be seen in a holistic way. As said earlier, many see the GDPR as an accelerator of the integration of security, privacy, information governance, compliance and more. And that is indeed a benefit.
GDPR compliance -step 5: Managing/evaluating and improving/adapting
Once the plans are rolled out, the work is not done. In fact, if we forget the EU GDPR as such and look at the integrated approach regarding security, privacy, information governance etc., you’ll notice that we’re actually looking at a cycle.
So, on top of managing what we’ve done, evaluating our efforts with clear KPIs there will always be a need to improve and adapt.
There are several reasons for this:
- New employees will enter the organization.
- New technologies will be deployed and touch upon personal data: whether it’s the cloud, Big Data or the Internet of Things, you’ll need to evolve.
- Continuous improvement and adaptation is simply a given, certainly in a changing digital ecosystem and a changing legal and geopolitical context.
The GDPR and enterprise information and content management
Information systems, data quality monitoring, information governance processes, business processes and so forth need to be conceived or redesigned with the privacy by design requirements and, among others, the aspects of consent and control of the GDPR in mind.
Governance is one of the many aspects of the information management and data management puzzle. Compliance, nowadays the main driver of the cybersecurity evolutions, means information governance and information management.
But of course there are more information management aspects to the GDPR. As mentioned all fields are converging and, in fact, with several topics we’ve mentioned in the cybersecurity part, we are already in governance and information/data management.
EU GDPR compliance from the information management perspective
Let’s also dive deeper into a benefit again here. We still live in a reality with siloed information sources and data-intensive processes, while integration is key to succeed in digital transformation from an information management perspective.
Moreover, many organizations have challenges to cope with the increase of unstructured data and how to make sense of it. Finally, in many business functions, you need a way to combine various formats and sources of data. Think about contact centers, for instance. Or insurance claims processes. While data lakes offered one solution in this regard, there are specific approaches for these various circumstances. For the contact center there are AI-enabled platforms that can deal with multichannel communications, for insurance claims processing there are case management solutions and so on. All these, by definition integrated, approaches, connecting information and communication silos and leveraging various forms of data, help you improve customer service, response times and simply business.
See the GDPR as a way to move in these better, integrated directions in case you haven’t yet. And then we haven’t even touched upon the benefits of revisiting your retention policies yet or the benefits of making sure that you have methods to make data easily searchable which doesn’t just make lives of your knowledge workers easier but isn’t a bad idea if an individual wants to gain access to his personal data.
Some elements from an information management perspective
- Mapping and classifying data. Many organizations don’t have clear visibility into the types of data (personal and others) they process. Moreover, insufficient classification makes it hard to implement the necessary policies. Where does all the concerned data sit across the organization and what is needed to have a single view and a fast and efficient way in case of compliance controls and potential questions?
- Mapping personal data and data flows. While knowing where data and, in the context of the GDPR, personal data sits is important overall, we obviously want to look at the various types of personal data. Some of that data is more sensitive. For example: it’s clear that financial data which can be abused when stolen with major consequences, is a bit more sensitive than some essential data for easy tasks. All personal data is created equal but some is more equal than others, to use George Orwell. Finally, also map the data flows whereby personal data is processed and document the various aspects of these flows: what, why, for whom (access!!!) and how long. With the GDPR people can ask which personal data are processed, where and how so documenting is crucial.
- The ‘how long’ brings us to data retention and erasure. Personal data sits everywhere. A traditional big challenges revolves around all the unstructured data/information/communications organizations have been hoarding across various repositories. That hoarding comes with many disadvantages as such but in the GDPR context it’s key to look at retention and also erasure (remember elements such as the right to be forgotten, portability and the right of access). What (personal) data do you actively use today, what data do you have and don’t use but could/should use to improve your business and what is ROT (redundant, outdated, trivial information) and can go, thus further decreasing risks?
Move towards a holistic information governance approach, deal with fragmented data and increase visibility.
GDPR compliance and information management technologies and strategies
On the solutions level of GDPR and information management we, among others, note consent management platforms, records management solutions, security solutions and artificial intelligence to name a few.
The latter is particularly interesting from an automatic classification perspective and to simply know where Personally Identifiable Information sits at all times. It’s one of the most powerful ways to be close to GDPR compliance demands although security strategies and information management strategies need to be revised.
As is mentioned in our article on the General Data Protection Regulation as a business strategy and information management challenge, the GDPR’s privacy by design means that you de facto move from an ‘open unless’ to a ‘closed unless’ enterprise information management and enterprise content management approach.
Simply said: instead of having a security model on the level of information management (or having none at all) whereby in principle everything is open for the teams unless decided otherwise for specific folders or resources, you do the opposite: what needs to be closed from the GDPR’s perspective, what can be open and how do we make sure what is open and where it sits.
GDPR compliance and cybersecurity
It is inevitable but also beneficial and about time: there are no more excuses to NOT increase cybersecurity maturity and go beyond outdated security approaches.
As said earlier, security cannot be an afterthought in an age where data is oil, personal data is whatever is worth far more than oil and digital transformation simply requires better security.
Without diving too deep in the details (for now) this means, among others:
- Embrace security by design, just as the GDPR requires privacy by design. Security by design means security as an omnipresent given, from the very start of products (imagine how many consumer IoT manufacturers would need to change), processes and people’s activities.
- Have a proactive and embedded security approach, including all aspects in the ubiquitous security perimeter reality (the perimeter is not gone, it is everywhere) in which all aspects matter (the edge, the network, cloud, the IT systems, data storage, databases, applications, you name it).
- Take a holistic approach to cybersecurity, starting from awareness and employee education (part of your mobile perimeter at the edge) and going all the way through your systems, processes and close to where (personal) data is generated and processed.
- Very possibly you will need to redesign your overall cybersecurity infrastructure with a focus on the just mentioned characteristics and in the GDPR context obviously on data flows and any process and risk factor where privacy and personal data can be involved (with breaches being a crucial, yet just one of several, dimensions).
- Go for real-time security possibilities, among others regarding the enforcement of security policies in areas such as device management, access (to data), the activities of users and so forth. Encryption of personal data also is emphasized by the GDPR.
- You need a unified view on what happens with data, data processes, Big Data environments (e.g. data lakes), regardless of form and structure, and single visibility for the Chief (Information) Security Officer, IT manager or whomever needs it across all operations, workloads and the IT infrastructure as such.
- Conduct regular testing. On top of a proactive cybersecurity approach with predictive capabilities that won’t be possible for everyone, pro-activeness also means regular and where possible continuous testing. From ethical hackers to penetration testing and beyond. Do penetration testing, among others on the level of your web applications and web services, deploy a vulnerability scanner on individual devices and the full organization, go for vulnerability management and an integrated approach.
- Look at mechanisms and solutions to prevent identity fraud (there are specific solutions in some countries, for instance to make sure that stolen identity cards or driver licenses can’t be abused).
- Conduct social engineering testing. Phishing is still an important way of obtaining personal data. Workers need to be trained on these tactics, social engineering and security overall. Also test how susceptible employees are to social engineering, using one of many phishing simulators.
Last but not least: bad things happen and we shouldn’t forget the breach notification duty of course.
In practice, this means you need to set up the necessary monitoring, auditing and alerting mechanisms, to do so. This is also a cross-functional task and there are solutions for legal to deal with it. You need incident management processes and a clear view of who needs to do what and where in case of a breach. Testing if they work well is not a luxury.

How the EU GDPR can benefit your organization: trust
On top of being the mentioned framework which is needed for growth in a digital economy which transgresses the borders of individual nations, there are several other ways how and reasons the General Data Protection Regulation benefits your organization if you do your GDPR compliance homework properly.
Some of these benefits have to do with optimization opportunities, others are societal and have reached a boiling point throughout 2016 and early 2017. We start with trust.
If data is the new oil, trust is the new oil well
We have reached a point in history where the technological possibilities and innovative capabilities, leveraging these new technologies, are about to explode.
The things we can do, as organizations, governments, individuals, marketers, manufacturers and so forth thanks to technologies in the space of Big Data, analytics, cloud, the Internet of Things, cognitive/AI, social and mobile, to name a few, already seem huge today.
The truth, however, is that we haven’t seen a thing yet. Despite getting major attention, the Internet of Things, for instance, is still in its early days. The volumes and variety of data which we started to call Big Data, are just some small droplets in the ocean of data that will soon be generated in science alone. Despite looking at this grandiose digital universe of data which we believe we see today and which is the common denominator in all the mentioned technologies and the many others we didn’t mention, we indeed haven’t seen a thing yet.
The many smart people who are working in several of the mentioned fields today know that and, as far as the digital transformation of industries and many aspects of our lives are concerned, they know the potential. For some it is reason for great optimism, for others it’s scary and for those who care it’s a mix of both.
Yet, for all that new oil, there is a big challenge that is happening right now right here and that needs to be addressed: trust.
It’s not just the new oil well but if it gets broken, anything we do in a digital society with that new oil, called data, is failed to doom. Without trust and transparency regarding what we are doing, there will be an inevitable backlash and to continue the oil well image, we might see some oil fields on fire.
With apologies for the doom scenario: the benefits of digital innovations and of data, put at work, are tremendous but we must keep people and trust in mind, because it matters and because the human emotion and ability to stop evolutions or rapidly adopt an entirely shifted mindset beats all data, technological transformation/innovation and predictions, no matter how big the data.
GDPR and trust: the state of trust in the digital age
There all ample signs of a backlash against the way we use data today and, in a broader perspective, of distrust regarding the parties that gather and process data and the digital evolutions as such.
We’ve mentioned it several times before, among others in a context of the importance to restore trust by leveraging trustworthy content (marketing) for trustworthy and transparent communications: the Edelman 2017 Trust Barometer, which shows a declining level of trust in all areas.
Other research indicates that even younger generations are increasingly vigilant regarding the ways their data is used and consumers are on the verge of potentially disrupting the state of privacy.
The General Data Protection Regulation, as a framework, offers a possibility to restore trust in the digital economy and, at least as important, enables organizations to improve their current data and security practices, which is crucial anyway in these times of hyper-connectivity where data as said has become more than just a crucial business asset and smooth and transparent processes lead to a perception of trust, efficiency and good business practices. Obviously, improving current practices and processes with security, transparency, efficiency and people in mind, is also good for the bottom line and the effectiveness of the organization (in a digital economy) as such.
Better security and information management lead to higher digital transformation success probability
Research has clearly indicated that involving security from the very start in any digital business transformation project with a role for (new) technologies, leads to more and faster success.
Moreover, security by design, is simply beneficial (and a must) and security is a digital transformation enabler and accelerator. No matter the stage in which your digital transformation is or the aspects you transform (business processes, customer-centricity, the development of new capabilities, tapping into new business models and so forth), things have to run smoothly and in a reliable way, guaranteeing not just business continuity but also protecting those assets that drive the digital economy: data and people.
Moreover, just imagine how better security practices, by design, along with better privacy practices, as the GDPR requires by design as well, would advance various markets where the Internet of Things clearly has transformational potential and leads to tangible outcomes, today mainly in an industrial Internet of Things context. The same applies to other, related sets of technologies and, most importantly, how they are leveraged to reinvent business models or optimize existing processes, customer-facing operations and so forth.
On an information management level, which is also key for GDPR and is closely related with security from the data and governance perspective (among others), the various audits, plans and deployments regarding enhancements for the General Data Protection Regulation, de facto include data discovery, integration of silos, a need to look at what data you “have” and where it resides, smoother reporting and search possibilities, improved data mapping, retention policies and so much more.
It is an undeniable fact that one of the major hurdles in many digital transformation projects revolves around poor data and information management practices.
We’ve reported on this several times so see the General Data Protection Regulation as a way to do better here too.
Holistic (customer) optimization benefits of the EU GDPR
When you do a, by definition holistic, strategic exercise regarding all aspects of how you deal with personal data and thus also customer data, with the interest of the latter in mind you are forced to 1) identify the data (and in the process find unstructured data you haven’t leveraged and/or gain better insights) and 2) revisit the ways you process data.
If you take this exercise seriously with relevance, consent, privacy and the mentioned holistic approach in mind, it’s almost inevitable that you also detect numerous opportunities to optimize several customer-facing activities. Maybe your contact center will finally dispose of all the data required to better serve and service customers, maybe you’ll improve marketing efficiency as your staff will learn not to think about a name and email address on a list as nothing more that that.
We can go on for a while.
Challenges and issues regarding the GDPR
Probably we’ve tackled enough challenges already and in the lists with resources you’ll find plenty more. However, there are challenges, concerns and issues that need to be looked at.
It won’t come as a surprise that there are frequent calls from all kinds of industry organizations to clarify not just the sometimes somewhat vague terms in the GDPR (such as “disproportionate effort”) but also to look closer at some practical issues that arise.
We’re not naive and it’s clear that, while the General Data Protection Regulation offers benefits, it also comes with loads of uncertainties, practical challenges and for some industries more than for others with serious inconveniences to say the least.
Several industry associations look at these issues as they learn them from their members and experts and also lobby for flexibility or de facto changes.
While we can’t cover all challenges, issues and initiatives it’s good to look at the issues as they are raised a bit everywhere and see whether they apply to you as well. By way of an example we covered four General Data Protection Regulation issues as they were raised in March 2017 by a few marketing/advertising associations. Some can be of help for your business too.
More articles on the EU GDPR and GDPR compliance
GDPR fines, GDPR staff awareness, GDPR compliance, controllers and data subjects. Are you lost? Then also check out the following resources on the GDPR.
GDPR compliance: a strategic business and information management view
This article in fact combines two important aspects with regards to the GDPR, which we have briefly tackled before.
3 stages in an end-to-end strategic business information management GDPR compliance approach: 1) an awareness stage to empower your people and users, the weakest link in any ECM and security project; 2) an assessment and methodology stage to detect the risks and make a plan to solve them and 3) an implementation stage: rolling out, monitoring and improving.
- On one hand it looks at the strategic business aspects of the General Data Protection Regulation and offers a no-nonsense approach of how to become as GDPR compliant as much as possible with a prioritization of what to do first and how to progress, showing that you did as much as you could to minimize personal data risks and thus also GDPR fines.
- On the other hand it looks at GDPR compliance and the various strategic steps to take from mainly a personal data and information governance and information management perspective. Starting from the essential stage (and quick win) of General Data Protection Regulation awareness to risk analysis, effectively implementing privacy by design, enabling the right of erasure with retention schemes and records management and for really advanced GDPR compliance: automatic classification!
GDPR awareness and GDPR staff awareness
Given the fact that GDPR compliance really should start with GDPR awareness and GDPR staff awareness, this article dives deeper into the why and how.
Whether companies will successfully navigate the GDPR regulation hinges on their willingness to embrace privacy by design. They must also understand that good security and privacy processes can provide a substantial competitive advantage and be a driver in gaining consumer trust, in addition to being driven by regulatory requirements (Peter Gooch, cyber risk partner, Deloitte)
While GDPR awareness is low-hanging fruit and a quick win on the road of GDPR compliance it does require executive involvement and a clear focus on people and involving all employees as personal data protection is a matter of the whole organization. Unfortunately, as the article explains, the departments that are most often involved in GDPR compliance are IT, security and legal.
So, what is needed to have a culture that supports privacy by design and a cross-organizational GDPR awareness whereby the value of personal data is really understood? Knowing that consumers do expect personal data protection (and in case of breaches there are more consequences for your business reputation than fines) and knowing that a culture of personal data protection even must stretch beyond the organizational borders (because you have partners, suppliers and so forth who also need to be in order to avoid liability discussions and more), it’s an important read.
GDPR compliance failure starts with wrong perceptions
Many organizations are quite confident that they are GDPR compliant. Unfortunately, there are disconnects on various levels which lead to failure in complying with GDPR.
It starts from a lack of understanding (one disconnect) the General Data Protection Regulation and goes to a lack of executive buy-in as also found in this article on GDPR and cloud and a lack of having the essential data governance strategies in place.
Do not become one of many organizations where there is a disconnect regarding perceptions about how GDPR compliant you are and the reality of your General Data Protection Regulation compliance. Check out if you are indeed properly prepared instead of trusting on perceptions over facts.
GDPR and personal data protection: everything about data subjects, personal data, sensitive data, personal data identifiers and more
The General Data Protection Regulation is about the protection of personal data of data subjects. That much is clear.
However, in practice we find that many people don’t know the meaning and importance under GDPR of personal data, the identifiers that the data subject even more identifiable and/or make personal data sensitive data, the importance and meaning of pseudonymisation, encryption, all the new identifiers and even what a data subject is under GDPR.
This article takes a really deep dive and makes all those terms and their role and meaning clear!
GDPR fines and penalties: guidelines
We talked about the GDPR fines previously. There are two groups of administrative fines in the GDPR: for one category there is a maximum of up to 20 million euros or 4 percent of annual worldwide turnover, for a second category it’s 10 million euros or 2 percent.
For both groups the additional stipulation is that the highest of both will be applied. The GDPR text does has specific articles on the general rules with regards to both sets of fines. They can be found in Article 83 of Chapter 8 of the text.
However, many find it rather unclear. In October 2017 the so-called Article 29 Working Party came up with guidelines for supervisory authorities for the application of fines and penalties under the General Data Protection Regulation. You can find them in this article on GDPR fines and penalties. Furthermore, we look at whether companies think they are financially prepared to pay potential GDPR penalties and at the value and usage of cyber insurances. And of course there are some reminders on how to avoid GDPR fines and start getting GDPR compliant.
If you want to know what the GDPR text says about fines and penalties then you might want to check out the mentioned Chapter 8 of the text which is all about GDPR remedies, liabilities and penalties and contains Articles 77 to 84.
GDPR compliance and becoming GDPR compliant: FAQ
We often get questions about the EU GDPR that might seem obvious at first sight but do deserve an answer of course. Many of these questions concern GDPR compliance, what is the deadline for General Data Protection Regulation compliance and what happens when you’re not GDPR compliant in due time.
What is GDPR compliance?
GDPR compliance means that an organization adheres to the rules of the General Data Protection Regulation and is capable of meeting the data subject rights and organizational duties which are stipulated in it. When people speak about GDPR compliance they often mean that personal data breach risk protection measures and all the other risks and rules to comply with are perfectly covered.
However, there is no perfect security or protection in the digital age where sometimes hackers even outsmart security companies, hacks are sometimes organized by criminal groups and there are even state-sponsored attacks. With data and technology being so important some countries use technology for cyber warfare.
Moreover, data can never be 200% perfectly protected and there are myriad other reasons why breaches and non-compliance could occur with people being the weakest link. Even if you take all possible precautions one of your workers could make a mistake and, for example, have his laptop stolen.
Therefore, organizations must be able to prove they did and continue to do (also after the date when GDPR applies) everything they can to be as compliant as possible. This includes knowing where personal data sits in the organization, making sure (and being able to prove) that consent is given under the legal conditions foreseen in the General Data Protection Regulation, being able to protect the obtained, processed, stored and – under specific conditions – shared personal data against breaches, abuse and misuse and being able to respond to the requests and rights of data subjects. If any of these abilities are not in place, the fines and penalties can be high.
When does GDPR apply and what is the GDPR deadline for compliance?
The General Data Protection Regulation has been adopted by the EU Council on 8 April 2016 and adopted by the European Parliament on 14 April 2016. The official texts are available since 4 May 2016. Since that data the GDPR text can also be consulted in 24 official languages.
The General Data Protection Regulation already entered into force in fact but it applies as from 25 May 2018. The GDPR deadline for compliance is 25 May 2018 as well.
However, it doesn’t stop then. Being GDPR compliant is an ongoing effort. Moreover, as we saw in the road towards GDPR compliance and the reality in the field it’s certain that a lot of companies will not be GDPR compliant. That’s why it matters to have a plan and build upon that plan from the risk perspective and with the ability to demonstrate you took – and still are taking – GDPR compliance steps. But of course in case of a personal data breach or control it’s best to at least be as compliant as you possibly can by May 25th 2018.
What if an organization is not GDPR compliant by the EU GDPR compliance deadline?
Unfortunately, despite being officially published two years ahead of the deadline a large number of organizations is far from close to being compliant with the General Data Protection Regulation.
While it is certain that there will be cases of severe fines to set an example it is also certain that organizations need to continue – and in some cases even start – with efforts to get as compliant as possible and to continue doing so after 25 May 2018. Ideally, this starts with a stage of GDPR awareness in a broader plan. As fines and stipulations of the GDPR are related with the risks from the data subject perspective and a focus on particular categories and usages of personal data, among others in industries where many personal data are processes, it is important to start from the viewpoints of risks and have a clear plan of action with documented steps. A risk analysis is key, as is a strategy and staff awareness. The General Data Protection Regulation also starts from the risk and data subject perspective.

Some organizations prefer to insure themselves but even then working towards compliance is important as you don’t want to be that company that is known to its customers and the world as being totally not GDPR compliant, let alone suffering from a breach with an additional clear lack of understanding of and focus on personal data protection, which is as much about leadership, culture, people, processes and respect as it is about security, information management and other technological ways to work towards compliance.
Are there specific ways that help in demonstrating GDPR compliance?
The GDPR Articles are full of rules regarding compliance with the Regulation and the duty to demonstrate GDPR compliance. If you add the recitals of the final GDPR text to it, there is even far more on not just compliance duties but also on those various ways that help organizations (controllers and processors) to show they took the necessary steps in demonstrating that compliance.
These ways of demonstrating GDPR compliance obviously are as important as becoming GDPR compliant as such. It is not as if on May 25th all organizations will be checked for GDPR compliance. However, when controls are done, complaints of data subjects are lodged, personal data breaches occur, there are clear infringements with regards to the principles of data privacy (by design and by default) and personal data protection, demonstrating GDPR compliance becomes essential.
In each GDPR compliance strategy, the ways to demonstrate compliance should be taken into account and the perspective of risk with regards to the rights and freedoms of data subjects are key in it. We’ve covered ample known and less known ways to demonstrate GDPR compliance before. Asking a DPIA is seen as a way to demonstrate compliance, asking advice to supervisory authorities as well, then there is adhering to approved codes of conduct or certification, the list goes on. We’ll add some more as the deadline of GDPR compliance approaches. We’ve talked about the DPIA and other ways so here is a bit more information on two ways to demonstrate GDPR compliance: those codes of conduct and certifications.
Adhering to an approved code of conduct to demonstrate GDPR compliance
Codes of conduct can be drafted by supervisory authorities and by private associations who represent categories of controllers or processors which conduct similar data processing activities or are active in specific industries which allow for such a code of conduct.
A code of conduct needs to be approved and once it is an approved code of conduct controllers and processors can decide to adhere to it. If they do so it is not just a factor that is explicitly taken into account as a way to demonstrate GDPR compliance but also offers additional benefits, among others in areas such as the perceived reliability of processors towards controllers who will select processors based upon their degree of sufficient safeguards and GDPR compliance and cross-border transfers.
Do note that adhering to a code of conduct comes with responsibilities as well of course. It would be too easy to adhere to a code of conduct as a demonstration of compliance and then not care too much anymore. That’s why there are also monitoring bodies who check if you live up to the code of conduct.
Certifications to demonstrate GDPR compliance
The General Data Protection Regulation rules regarding certifications are relatively comparable with those regarding approved codes of conduct. However, a certification of course is not the same as a code of conduct. What both have in common in the scope of GDPR compliance is that also certifications are ways to demonstrate GDPR compliance and explicitly recognized as such.
You might have followed some sort of GDPR certification course already or intend to. Do note, however, that certification needs to meet certain specifications, as do codes of conduct so beware of the how and where.
Just like codes of conduct, certifications are ‘promoted’ by the General Data Protection Regulation as ways to not just demonstrate compliance but also as a token to any stakeholder that your organization is aware of what it needs to do in order to conduct lawful processing of personal data.
Next in regulations and compliance: EU DORA Digital Operational Resilience Act
Top image: Shutterstock – Copyright: symbiot – Alarm clock image: Shutterstock – Copyright: Carlos Amarillo – Awareness image: Shutterstock – Copyright: Kunst Bilder – All other images are the property of their respective mentioned owners. Although the content of this article is thoroughly checked we are not liable for potential mistakes and advice you to seek assistance in preparing for EU GDPR compliance.

