Phishing is one of the oldest forms of cybercrime and remains a massive threat to Internet users and organizations. In the more than two decades that phishing has been around, it has changed in several ways though the essence remains the same. An overview of phishing in 2022 and the years to come.
For the next few years, many cybersecurity challenges stem from the continued expansion of the enterprise attack surface in an increasingly digital world.

Geopolitical changes, unexpected events, and increasing digitalization continue to create new challenges as the digital transformation of our societies continues. And these are just some of the factors causing new risks and bringing existing cyber threats to the forefront.
Many methods and threats that cybercriminals use and that we have known for a long time also continue to exist. These are, of course, the “old” threats that still work after all these years and, often with more recent refinements and sophistication, continue to deliver what criminals expect from them.
This is undoubtedly true with phishing, a long-standing method of cybercrime and online scams that is far more powerful than a simple look might suggest.
What phishing is and means in practice
Moreover, phishing is not only on the rise for many years. It also has proven to be a real headache again in 2022, with several large attacks that fit in complex attack scenarios.
Examples include the case of Cisco (in combination with voice phishing or vishing, as Cisco explained) and Twilio (where we had a smishing or SMS phishing scam). Technology companies indeed do not escape the phishing dance either.
Phishing is a crime employing social engineering and technical subterfuge to steal consumers’ personal identity data and financial account credentials. Social engineering schemes prey on unwary victims by fooling them into believing they are dealing with a trusted, legitimate party, such as by using deceptive email addresses and email messages. These are designed to lead consumers to counterfeit Web sites that trick recipients into divulging financial data such as usernames and passwords. Technical subterfuge schemes plant malware onto computers to steal credentials directly, often using systems that intercept consumers’ account usernames and passwords or misdirect consumers to counterfeit Web sites. (“Phishing Defined,” APWG)
Phishing is a form of scam in which criminals (predominantly) use online and digital channels to “fish” for confidential information of potential victims, such as usernames, passwords, credit card details, and other credentials. They do this by impersonating someone else and using fraudulent messages, online tools, and fake sites to obtain that confidential information under pretenses.
Phishing is a form of social engineering. That’s a broader term for various activities where criminals predominantly want to induce you through psychological manipulation to share confidential data or do something that is essentially a security breach and might fit within the framework of a more significant multi-step breach.
In most cases, email is still used as a vehicle. Online social engineering or phishing is an email-based attack intended to trick individuals into performing an action beneficial to the attacker (e.g., clicking a link or divulging personal information) according to NIST Special Publication 800-12 Revision 1. In the document, NIST defines phishing as a technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a website, “in which the perpetrator masquerades as a legitimate business or reputable person”.
The illegal use of stolen credentials can be applied at multiple stages of an attack chain. Some attacks culminate with the theft of a password database, other attacks use stolen credentials to gain access to an application or network, while other attacks use the credentials to send internal spear phishing emails from valid corporate accounts (David Warburton, F5 Labs)
There are, as per usual, several other definitions, especially with a practice that has existed for over two decades. It’s clear, for instance, that smishing and vishing on their own don’t use email as we know it. And then there are all those social channels enabling phishing attempts (e.g., WhatsApp fraud). One could say that, just like consumers, criminals are omnichannel or channel-agnostic these days.
Regardless of why phishing is used and the precise context in which it is used, tricking and manipulating people into trusting and believing is a central feature. Pretending to be a trustworthy, often well-known, and legitimate party is essential in all forms of phishing, where a sophisticated and targeted approach tailored to the ‘victim’ leads to ‘better’ results. Without the attackers coming across as a trustworthy party, victims would, of course, not share their credentials or take any other action desired by the criminals (whereby malware – including ransomware – can be spread too). We should add that sometimes people still fall into the trap of the most incredible scams, which is why they haven’t gone either.
While compromised credentials continued to reign as the most common cause of a breach (19%), phishing was the second (16%) and the costliest cause, leading to $4.91 million in average breach costs for responding organizations (IBM, 2022)
Phishing attacks, as briefly mentioned, are often a start or part of broader attacks that can take all sorts of forms and lead to significant data breaches and other security incidents combining various techniques, as with Twilio, Cisco, and countless others. But sometimes, their intent is also limited. For example, criminals sometimes use phishing to ‘simply’ collect extra data from people to sell it to other criminals who then use it for other purposes.
However, we cannot emphasize enough how phishing (and other forms of social engineering) is used, and the objectives it serves today can be particularly sophisticated and done in many steps going for giant attacks and profits. It fits the zeitgeist of increasingly complex attacks with newer methods. At the same time, it is easier than ever for criminals to use phishing to trick people out of their personal data. It all depends on the methods, targets, who is behind it, etc. To make it easier for criminals than ever, there is even such a thing as Phishing as a Service, as we shall see further on.
The evolution and present of phishing – data and trends
Here’s a brief overview of the state of phishing with an update on how often and why it is used and some data from the recent past.
Phishing during a pandemic – 2020 and 2021
As with just about every other form of cybercrime, we saw a sharp increase in phishing attacks in 2020. The number of phishing incidents rose 220 percent during the peak of the (first wave of the) corona pandemic (officially declared a pandemic by the WHO on March 11, 2020) compared to the average a year earlier, according to F5 Labs’ Phishing and Fraud Report.
While phishing has long been one of the most common tactics used in cyberattacks by sophisticated threat actors, it’s becoming more accessible to non-technical cybercriminals due to a maturing underground marketplace for attack frameworks and services. By selling their pre-built phishing tools and services on the dark web, cybercriminals are making it easier to deploy phishing scams at scale, creating a greater chance for more phishing activity in 2022. (Zscaler)
And that had a lot to do with corona, a dream for phishers. After all, recall the mental and psychological manipulation aspect of phishing and how people were overwhelmed with questions and, of course, often emotions during the first wave of COVID-19. The study further revealed that the number of phishing incidents for 2020 increased by about 15 percent.
The main target of pandemic-related phishing attacks was obtaining donations to non-existent charities in the fight against the (consequences of) the virus. In second place was the classic acquisition of credentials, and malware delivery ranked third.
But phishing also continued – and continues – to grow outside the context of the pandemic, of course. In late 2021, another report from F5 Labs, the 2021 Application Protection Report, showed that phishing ranked second among the most common initial attack techniques that led to a successful data breach.
More recently, in July 2022, phishing was again found at the top of a list; as the cause of breaches with the most expensive consequences, according to the then published annual cost of a data breach report by IBM and Ponemon Institute. Again, it finished as the second most common cause of breaches with 16 percent, just behind compromised credentials which caused 19 percent of all breaches. You can immediately see how vital those credentials – and thus social engineering – are.
Emerging phishing vectors, such as SMS phishing, are increasing faster than other methods as end users become more wary of suspicious emails (Zscaler)
Cloud security company Zscaler reported in April 2022 that the number of phishing attacks had again broken records in 2021.
Zscaler noted quite correctly that phishing continues to increase each year because it is so accessible, in addition to the fact that it simply continues to work. There is always something new around us that enables cybercriminals to play with people’s emotions and sense of urgency, creating victims and getting their credentials using these events as an “argument” and trigger. The COVID-19 pandemic was probably the most important event of the last few years in that regard, but of course, it is far from the only one (it suffices to look at the ‘most read’ news stories during a given period), and some “topics” remain on the minds of people (their income and finances, for instance). The pandemic was also a vital enabler for hackers, scammers, spoofers, and phishers since the adoption of digital tools skyrocketed with many people using applications for specific tasks for the first time ever, the rise of remote work and hybrid working and IT and security teams being overwhelmed and under pressure to make a ‘digital switch.’
Because of this focus on current/important events and what concerns people, you also often see shifts in the sectors that are most “victimized” by phishing. After all, it is not only the unwitting individuals who are persuaded to hand over their data which are victims. So are the companies, brands, organizations, and so on that the criminals pretend to be.
In addition, companies are also attacked in more complex scenarios in which phishing plays a role. Both Cisco and Twilio are examples of this that we will take a closer look at. Cisco, by the way, nicely shows how you can also be very transparent about the course of an attack you are the victim of and contribute to a better understanding of the ever-evolving cybersecurity reality.
The financial sector was the most frequently victimized by phishing in Q1, with 23.6% of all attacks. Attacks against SaaS and webmail providers continued to be numerous. Phishing against cryptocurrency targets inched up to 6.6% of attacks (APWG, Phishing Activity Trends, 1st Quarter 2022)
Phishing in 2022
Another report with data on phishing in 2022 comes from the Anti-Phishing Working Group (APWG). That’s a not-for-profit organization where more than 2,000 various types of organizations work together to combat identity theft and breaches resulting from techniques like phishing and email spoofing.
The APWG Phishing Activity Trends report for Q1 2022 observed a total of 1,025,968 total phishing attacks for the first quarter of 2022, a new record. March 2022 also set a record with the highest monthly total ever: 384,291.
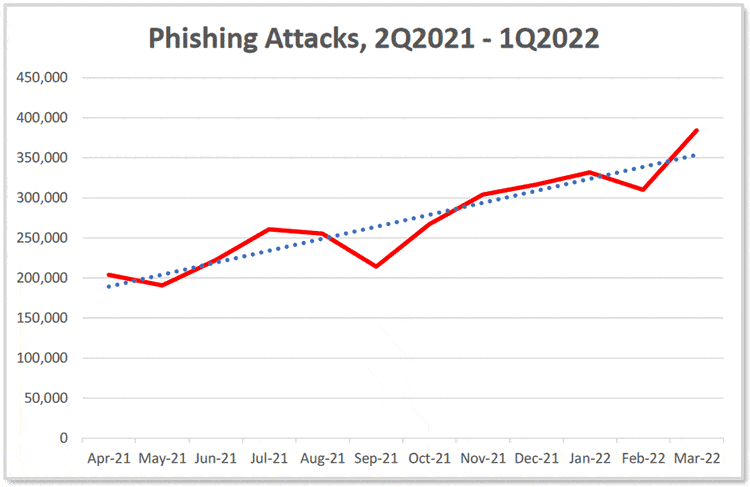
This means that the number of phishing attacks in the first quarter of 2022 has more than tripled since early 2020.
According to one of APWG’s founders, OpSec Security, phishing remains highest in the financial sector. Attacks against webmail and Software-as-a-Service providers have dropped to second place and eCommerce/retail to third (after the fourth quarter shopping season, when eCommerce/retail, for obvious reasons, are more targeted).
The future of phishing – a glimpse
The low threshold of phishing has to do with something else as well. It is becoming easier and easier for criminals to set up reasonably sophisticated phishing attacks, also in terms of technical resources. Zscaler’s research made an interesting observation: Phishing-as-a-Service has now become the primary source of attacks where pre-built attack tools lower the technical threshold for criminals.
So it is and remains a constant struggle, especially in those highly sophisticated attacks where phishing is a small part of a complex and carefully constructed, often longer-lasting, attack with many lateral moves.
Moreover, as mentioned earlier, new forms and variations involving various channels and tactics are constantly emerging. The more people learn to recognize phishing via mail; the more criminals come up with variants and other attack vectors. For example, we know from Zscaler’s research that SMS phishing or smishing is on the rise pretty strongly and per IBM targeted phishing campaigns that added phone calls, what vishing or voice phishing is all about, were three times more effective.
It is important to remember that cyber crime and attacks, whether phishing or anything else, are becoming less and less linear and uniform. Thanks to the growing attack surface, more extensive third-party networks (and associated third-party risks), digital ecosystems, and the combination of attack tactics and threat vectors, criminals can be genuinely sophisticated as they increasingly focus on large profitable attacks with many (prominent) victims whereby they take the necessary time to strike.

This is why a proactive and integrated or holistic cybersecurity and cyber resilience strategy is so important, starting from risks (integrated risk management) and acquiring a complete vision of all threats by combining various methods.
Phishing, like other threats, has become part of the vast toolbox of cyber criminals in addition to being a threat as such. And it is right there that the future of phishing lies, along with all the mentioned ‘innovations’ such as Phishing as a Service, smishing, vishing, spear phishing, and more: in its place and role. And, of course, things will continue to happen that will continue to enable the more classic phishing attacks and will continue to work for quite some time.
Phishing is a technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a web site, in which the perpetrator masquerades as a legitimate business or reputable person. (NIST)

