Cybercrime and cyberattacks continue to rise with ever more data breaches, sophisticated phishing and crippling ransomware attacks. A broader security strategy is needed as the attack surface grows, and we rely more on digital technologies in all areas of business and industry.
An overview of the cybersecurity challenges and evolutions and how cyber resilience can help organizations prevent, detect, respond, and recover.

The face of cybersecurity is changing. Cybercrime has become increasingly prevalent and sophisticated. Moreover, the stakes are higher as we live in a data-driven and connected age where big data and the Internet of Things (IoT) are increasingly leveraged across business functions and sectors.
In essence, digital transformation is all about turning data into knowledge, insights, and actions for numerous purposes (remember DIKW). While with IoT, we’ve added ample opportunities to serve even more goals by adding data from ‘things’, at the same time, we’ve grown our digital footprint and thus the attack surface and risks for cyberattacks. Technologies such as cloud computing and various forms of artificial intelligence serve as enablers to better create value and transform. Yet, they as well pose challenges on a cybersecurity level. Moreover, some technologies are leveraged by cybercriminals to get better results.
The increasing sophistication, importance and impact of cybercrime and data breaches
Just one example: in the same way as we leverage artificial intelligence (AI) to detect anomalies and prevent cyberattacks, AI is increasingly used by hackers and others as a way to learn how cybersecurity solutions work.
On top of this increasing sophistication in cybercrime approaches, data breaches and cyberattacks become ever more impactful and can have tremendous costs while negatively impacting business continuity. New regulations, among others on the level of personal data protection, such as the General Data Protection Regulation, increase the costs of data breaches even more.
Security teams get involved in digital transformation projects too late or not at all. The reasons and consequences are multiple – time to transform your security approach.
Last but not least, there is increasing awareness that the question isn’t whether cyberattacks will happen, but when they will and how organizations can respond and recover fast. It’s one of the reasons why cyber resilience has become such an important topic, on top of, among others, the need for business continuity (and business resilience) and keeping core IT systems function during attacks.
Whether we like it or not: security and cybersecurity in specific can’t be afterthoughts and can’t be addressed with just traditional ad hoc and limited point solutions. Cybersecurity has become a critical strategic priority in digital business. Moreover, to be able to innovate, transform, and realize their digital potential in regards to any given goal, organizations want security and resiliency approaches that enable them to focus on their business and the continuity of it.
Tackling the cybersecurity maturity challenges to succeed with digital transformation
If enterprise IT and digital technologies play such an essential role in digital transformation, then why are there still such cybersecurity gaps?
Why are there gaps between the reality of cyberattacks, cybercrime, and awareness regarding the crucial role of security on the one hand and preparedness and cybersecurity maturity on the other? Is security present enough in digital transformation strategies? Is it being tackled too late? And, if so, why? And is cybersecurity alone enough? Don’t you need a broader cyber resilience approach, including disaster recovery but also a more proactive instead of defensive approach?
The purpose of a security program is not to ensure we don’t get hacked; that’s an impossible goal. The purpose of a security program is to balance the needs to protect with the needs to run the business. (Paul Proctor at the Gartner Security & Risk Management Summit 2021 Americas)
The board is concerned about cybersecurity maturity – but lip service is not enough
ISACA, previously known as the Information Systems Audit and Control Association, found that 82 percent of respondents “report that their enterprise board of directors is concerned or very concerned about cybersecurity” in its State of “Cybersecurity – Implications for 2016” report, conducted with the RSA Conference.
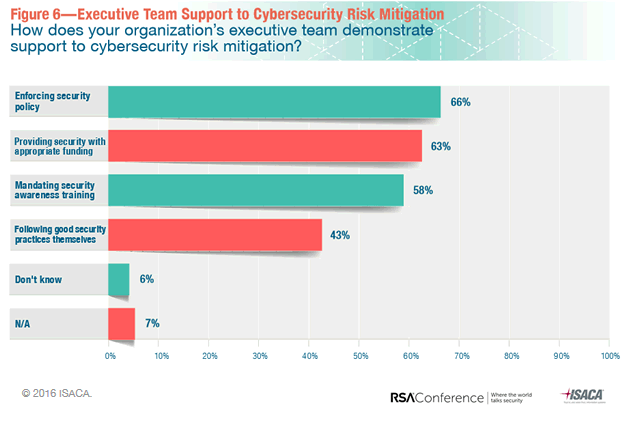
And, although it also found that executives are more supportive and active regarding security policies and practices, the reporting structure for security didn’t mature. Only 21 percent of CISOs (Chief Information Security Officers) report to the CEO or board.
Moreover, executive teams aren’t really always given the best example as only 43 percent of execs are reported to follow good security practices themselves, the report says (PDF opens). There is still ample room for executives to support cybersecurity risk mitigation as the graphic below shows. As companies increasingly approach cybersecurity from the risk management – and, increasingly, integrated risk management – perspective with cyber resilience being a more recent and more holistic approach it’s important to bring cybersecurity and cyber risk to the next level, including third-party risk management.
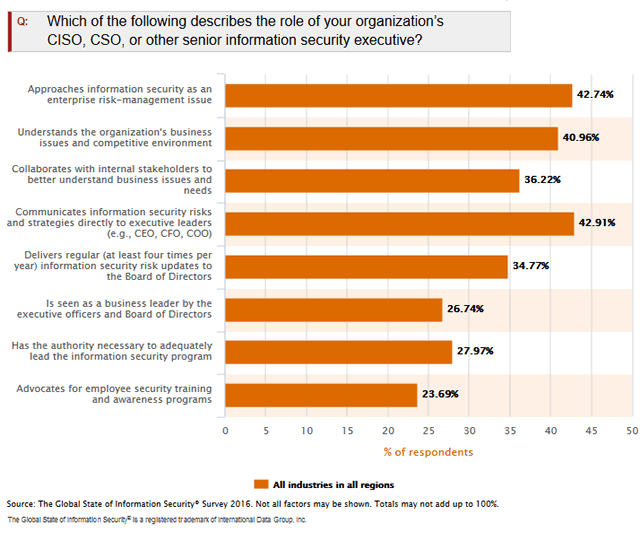
There is a bunch of similar research but there is also reason to be optimistic as leadership awareness levels regarding cybersecurity rise and ever more senior information security professionals do approach information security as an enterprise risk-management issue and communicate information security risks and strategies directly to executive leaders (respectively 42.74% and 42.91%) as PwC’s “The Global State of Information Security® Survey 2016” found. On the other hand, this means that for the rest this is not the case (yet).
Gartner recommends a much tighter collaboration between CIOs/CISOs and business execs on multiple levels with cybersecurity as a business risk and business decision.
Security maturity and optimization: perception versus reality
In the 2015 edition of its Annual Security Report, Cisco mentioned that the gap between the security reality for IT (and the business) on one hand and the perception of the boardroom regarding security on the other is still significant and needs to be bridged.
While almost two-thirds of the CISOs feel their protective processes are optimized as good as possible, less than half of SecOps (security operations) managers agree with this statement. Note: as said many CISOs report to the CIO who tends to be in general more concerned about the IT aspect than the CEO to whom relatively few CISOs report as mentioned earlier.
The Cisco report also shows that while 90 percent of organizations feel pretty confident about their security approach, their past breach record doesn’t really reflect that. It shouldn’t be a surprise that organizations with the best security setups and strategies also have execs who understand cybersecurity is an essential business priority in this digital day and age.
Why cybersecurity maturity isn’t what it should be in the digital business and transformation reality
The question remains: why those gaps? As usual there are many reasons. Below are a few reasons – and ways to address them.
Security as a must – we rather avoid
Let’s face it: everyone thinks security is critical but few people like to be confronted with it, let alone “see” it in the devices and platforms they work with.
The user experience matters. Performance and agility matters. And, yes, security matters, as long as it doesn’t influence these other factors. It’s probably the reason why we should think security first as well in our transformation and digitization efforts and why security is a bit becoming built-in everywhere from the holistic vendor perspective.
While almost two-thirds of CISOs feel their protective processes are optimized as good as possible, less than half of SecOps managers agree.
Still, many organizations keep steering away too much from the issue of security and avoid being confronted with it, despite saying it’s crucial. A mentality shift is needed. In the digital transformation reality the focus is a lot on speed, optimization, automation, innovation and all those other – intermediary – goals.
But it should also be on security (and of course compliance). If we want to reap the full benefits of transformation, innovation and digitalization, we also need to take that crucial security part into account because without it we forget the fundamentals, now more than ever. Security is a must. Period. And we need to stop looking at security as a cost center or from an archaic perspective.
Security as the enemy of digital transformation
Digital transformation is about change, agility, speed, connectivity, real-time economy, customer expectations, disruption and all those “hot” things we just mentioned. Security in the eyes of many stands in the way of all this.
It’s about rules and regulations, protection, defense (even if in reality cybersecurity becomes pro-active and offense), training, awareness, boring stuff (to some) and a layer that some believe to slow down the “sexy” digital transformation initiatives.
Marketing wants a new way to transform how it markets and serves customers or optimizes customer experience, it doesn’t want security to poke in there. Well, that too unfortunately is not really an accurate view anymore. Security experts know very well that users don’t want experiences, speed, innovation and performance affected by security solutions. Guess what: it doesn’t have to (anymore) and can even be done in the cloud. Still, security tends to get called in quite late in digital transformation projects. That’s also what research by Dell and Dimensional Research found. According to the research a majority of respondents feels that the security team gets involved in digital transformation projects too late. Among the reasons: execs are scared that their digital transformation efforts cloud be blocked by (the intervention of) security. That doesn’t seem like a valid excuse to us, at least not with today’s security solutions and certainly not by pretending security isn’t crucial.
Security and the technologies of the digital transformation economy
With the research from Dell and Dimensional Research we also enter the arena of technologies and IT domains were digital transformation is often taking place.
And it seems that there is not always a great relationship between security and some of these technologies. Initiatives in the space of the Internet of Things are probably among the most ‘obvious’ one. However, they’re not the only. While 97 percent of respondents say they invest in digital technologies such as mobile (or better: mobility), cloud applications and infrastructures and the IoT, only 18 percent say security has been involved in all mobile, IoT, cloud and self-service initiatives. Ouch, especially as according to the research digital transformation can be accelerated by bringing security in earlier.
Other reasons why cybersecurity maturity and strategy are lagging behind
There is a bunch of other reasons why cybersecurity maturity isn’t what it should be and a strategy to enable the business to optimize and transform is lacking.
Yet, many of them have to do with cybersecurity and security overall. However, several can be tied with DX evolutions and goals. Among them:
Security requires strategy and prioritization
Security isn’t always easy and does not start by adding security controls but by prioritizing the most critical processes, systems and potential sources of attacks or vulnerabilities. Needless to say that in the realm of the Internet of Things, vulnerability risks increase by the way. So, security needs a strategy and that is harder than adding a few firewalls of course.
The business case challenge of cybersecurity
It’s harder to make the business case for security than it is to, for instance, make the case for a digital transformation project in regards with the digital workplace, collaboration or customer experience.
Only 21 percent of CISOs (Chief Information Security Officers) report to the CEO or board.
You’re analyzing risks and dealing with the unpredictable. Rather than looking at the gaining back of costs, it’s sometimes better to factor in the losses if you fail to properly secure what needs securing. The problem is that you only truly know it when it happens and your business is interrupted, data stolen, compliance requirements breached or reputation down the drain.
Specific security skillset challenges
Skills is another one. It’s true that for many large organizations it’s harder to find the right security experts for specific applications, also in a context of digital transformation where often loads of data are involved and rather new technologies surface. But the shortage is an overall challenge (and there are partners to deal with it).
Security on the level of the user in a mobile age
The security parameter has changed as you know and as we mentioned. The cybersecurity perimeter is a but everywhere, the attack surface has grown and good old point solutions or firewalls alone don’t cut it anymore and in a digital transformation context protection at the level of the mobile user is a must.
The critical – but undervalued – role of data and information in transformation
The role of information and data, critical in digital transformation, is still all too often undervalued. Data and information are the lifeblood of the business and a source of revenues and new business models. In fact, the DX economy essentially is very much about 3 things: people, purpose and actionable information, regardless of the source. Unfortunately this isn’t reflected enough in the cybersecurity maturity levels of many organizations, nor in their compliance and/or governance measures, for that matter. According to the 2016 Ponemon Institute Cost of Cyber Crime Study infographic, information loss accounts for almost 40 percent of the damage of cyber crime and companies with an advanced information governance program reduce losses by $1 billion annually.
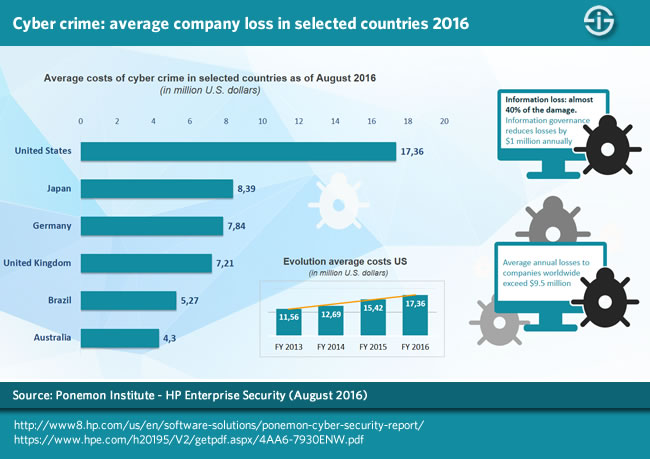
If you want digital transformation to succeed, changing the mindset, strategy and maturity regarding security is a must.
Involve security from the very beginning, make it embedded, look at data protection and privacy as assets and strengths instead of costs and give the CISO or other security executive a place around the table. In case you doubt: yes, CISOs are also expected to generate new business opportunities.
Changing security perimeters and cyber risks demand a holistic security approach for digital business
For many years now the security perimeter has moved, not just to the endpoints but to ALL levels of the bigger security picture.
Mobility, growing connectivity of technologies, people and processes, and the expansion of networks and clouds to include ever more data, devices and decentralized ways of working, have made the new security perimeter the “everything”. It ranges from more traditional perimeters that still exist to the user as a perimeter and even the Internet as a parameter. That’s an enormous difference with how cybersecurity was viewed upon only a few years ago.
The solution to address all these new cybersecurity risks and realities, which is not just a choice in this age of digital transformation and ubiquitous connectivity, as said, is by definition a holistic one that includes all the mentioned elements. But it’s also one that approaches security in different and more encompassing ways.
Most organizations are aware of this but as we saw there is a gap between realizing cybersecurity is now a key priority, moving into the boardroom, and needs far more attention and the ability to do so as there is an overall “digital crime gap”, including between the number and type of attacks organizations face and how they (can) react.
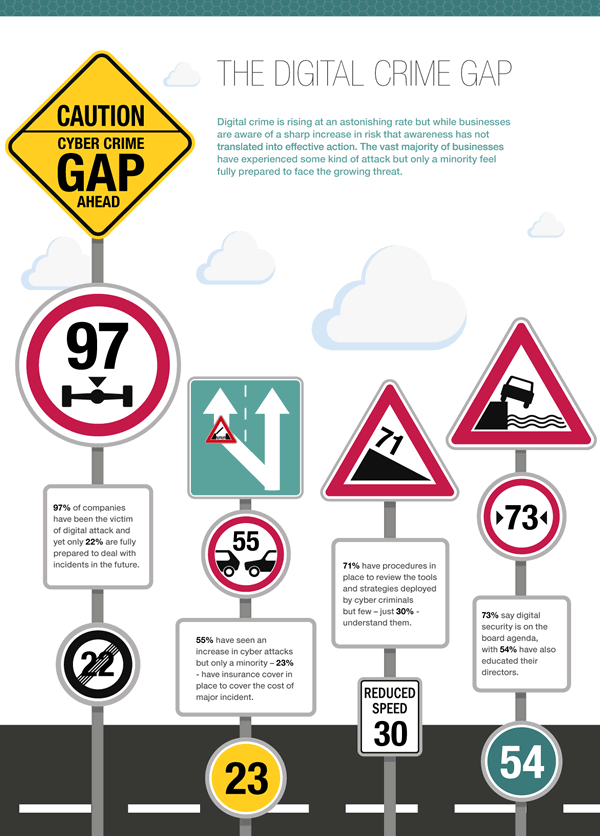
In the meantime, as organizations are putting issues such as security and compliance (with changing regulations), as well as business continuity, high on the agenda, it’s not as if the “bad guys” are sitting still either. Cybercriminals are smart, they know very well how to use new technologies and exploit vulnerabilities.
Waking up to the cybersecurity risks of the world-sized web
We don’t want to create a culture of fear or be scaremongerers but we want to emphasize how crucial it is to make your security approaches evolve and really put security at the center of your business and digital transformation efforts.
Let’s not be blind: state-sponsored hacks, far-reaching breaches and the rise in the number and diversity of attacks are all facts. Moreover, as we are including ever more digital devices and entities into our digital strategies with increasing hyper-connectivity (imagine the impact of the IoT) we need to stay ahead of the curve and not just catch up with smarter cybercriminals and increasing risks.

At RSA 2016, security guru and ‘veteran’ Bruce Schneier, who is known for his strong and sometimes even controversial statements on security went very far in waking all of us up to the new realities we live in (if you’re really interested in smart thoughts on the future of security and digital risks follow his blog).
The Register, which interviewed Schneier at the occasion of the event, had quite the headline: “Bruce Schneier: We’re sleepwalking towards digital disaster and are too dumb to stop”.
Schneier was mainly referring to the nascent so-called world-sized web, a term he deems horrible as you can read in the interview, but which essentially is used for the Internet of Everything as Cisco calls it, with the Internet of Things and its sensors and autonomous data processing units, coming as an expansion of the web and already hyper-connected reality as we know it today with mobile, cloud systems, multiple devices, a huge range of possibilities to connect anywhere anytime and across any type of network, and of course ‘users’ who want ubiquitous access to their apps, data and more.
Cybersecurity challenges and digital risks for the future
Below are a few essential cybersecurity problems and overall digital risks Schneier sees.
The design of the world-sized web: fragmentation and underestimation
In the interview with The Register he mentions the unknown security impact of that world-sized web which will change everything and, according to him gives more power to the powerful and is less being designed than created. The Internet of Things, among others, escapes from the traditional building and design of complex systems with a safety first principle to quote the interview on The Register. It is a fact that the IoT is not exactly the most standardized and designed phenomenon ever with a bunch of players, technologies, approaches and – indeed – quite often the lack of a safety first approach. Moreover, organizations – and people – are not aware enough yet of nascent evolutions in the context of cybersecurity, privacy, compliance and so on, which is clear in the underestimation of these challenges.
Predicting where technology goes doesn’t equal how it will socially affect us
We are relatively good in predicting where technology is heading but aren’t exactly good in how it will impact us socially, Bruce Schneier says on The Register. This isn’t new and not just about the future challenges of this world-sized web but we can’t say it isn’t true. Just consider: if you look at the current “security” climate and the “data” reality in a world where quite some weird things happen and people seem to be disconnected “mentally” in many ways (yes, we mean political evolutions and human behavior), one wonders what happened with the predictions on how social media would connect us more and – thus – help make the world a better place. Maybe it is for some and for Facebook but it sure isn’t in general. Have you seen the hate recently? This is just one example but there are many more and Schneier mentions some in the interview with The Register.
The complexity of a holistic security approach versus the focus of hackers
Hackers have a huge advantage over “defenders”. They need to exploit one vulnerability and done (although we see more and more real cybercrimals operating as digital entrepreneurs).
Companies, on the other hand, need to make sure that a myriad of security challenges is addressed and ever increasing connectivity happens in the most secure and holistic ways. That involves technology but also processes, strategies, various end points, code, devices and certainly people.
The dangers of the ‘computer world’ in the physical world
The collision of the digital and physical world is another topic that is dear to Schneier.
In an interview at RSA 2016 by ITProTV, Bruce Schneier reminds us how everything is becoming a 24/7 computer today and how the computer reality or digital reality affects the physical one. He mentions how these physical things affect us differently and are regulated differently. Think about medical devices and cars that are becoming computers instead of having computers on board. Cars can kill, he says. It’s not something to take lightheartedly and as you know cars as computers already have killed. This needs debate and regulation and not just explanation whereby human errors are sought and at all price we try to uphold the fact that it’s not the fault of ‘digital’ if something goes wrong as things will go wrong and have gone wrong. There is a reason why Tesla is looking so hard into the cause of the deadly accidents (with a focus on the human error), which were broadly reported on in recent months.
Raising cybersecurity and risk awareness
For Schneier there are many solutions to the various challenges such as disconnecting key systems and move to more distributed systems, putting limits on data storage and a need for governments to regulate technology more, with the involvement of the industry.
Of course there are different views than Schneier’s. There are also other risks and challenges. We’ve been reporting on some of them here and other sites with topics such as data and ethics/privacy, compliance as a key driver amidst changing regulations such as the European General Data Protection Regulation, challenges on the level of technologies and their potential impact, such as big data and artificial intelligence. But there are also positive evolutions and raising awareness is just one of them.
As the risk and attack surface is growing and we step into a world of more big data, algorithms, AI, technology, pervasive computing, the IoT and so on we need to have an open debate, not run away from it – regulators and industries together indeed.
We also can’t assume something is safe. Recently we saw an interview with someone on blockchain technology, which is rapidly gaining attention, also in securing the Internet of Things (more on IoT and blockchain). The fact that blockchain has proven to be secure as the interviewee said, doesn’t mean it truly is and will be when deployed in various contexts. We can’t assume, we can’t defend any technology whatsoever, shutting the doors for debates about its potential dangers, whether it’s related with security, society or anything else.
We have seen similar warnings before of course as Schneier’s but, given the accelerating growth and scale of the use of digital technologies across all areas of society, we need people like Schneier to warn us and make us act before things go wrong. In fact, there is an increasing focus on thinking ahead in cybersecurity, among others enabled by….artificial intelligence.
At the same time many organizations still have to close those gaps between their awareness regarding security and their capabilities and realities in the here and now. But that’s for later contributions.
Check out more articles on cybersecurity below
- CNAPP adoption: Cloud Native Application Protection Platform drivers
- SaaS security in an expanding reality of third-party connected apps
- The attack surface and importance of attack surface management
- What is TPRM? Third-party risk management and cyber risks
- What is vishing or voice phishing and why is it on the rise?
- IT security spending patterns and priorities Europe 2022-2026
- CISOs and CROs underestimate cyberthreats from digital ecosystems
- The state and challenges of OT cybersecurity 2022
- Security and risk management as an inherent part of business
- Penetration testing in an increasingly complex digital world
- The MITRE ATT&CK framework and evaluations explained
- The ransomware readiness gap and mitigation strategy challenge
- Software supply chain security: state and outlook
- The EU’s DORA Digital Operational Resilience Act for digital finance
- Splunk: top security issues facing the enterprise in 2022
- The state of cloud data security: challenges and recommendations
- MITRE ATT&CK for ICS shines light on industrial attack tactics
- OT and ICS security – the human dimension and organizational challenges
- Cyber resilience: business continuity and cyber incidents
Top image: Shutterstock – Copyright: BeeBright

