On September 24, 2020, the European Commission published the proposal for a regulation on digital operational resilience for the EU’s financial sector, further paving the way for a robust and resilient ongoing digital transformation of finance.
On May 11, 2022, a preliminary agreement was reached on the so-called Digital Operational Resilience Act, in short, ‘DORA.’ On 14 December 2022, the EU regulation’s final text was published and DORA entered into force on 16 January 2023. The DORA EU Regulation will apply as of 17 January 2025. So what do you need to know about DORA, and how does the Digital Operational Resilience Act impact various organizations within the EU financial world and its ICT and software supply chain of partners and providers?

The EU’s DORA in a nutshell: the ICT-related risks of financial entities and their ecosystem
The Digital Operational Resilience Act aims to be the regulatory framework ensuring that the EU financial sector and critical third parties providing ICT-related services to its various layers and players have sufficient capabilities to prevent and mitigate cyber threats.
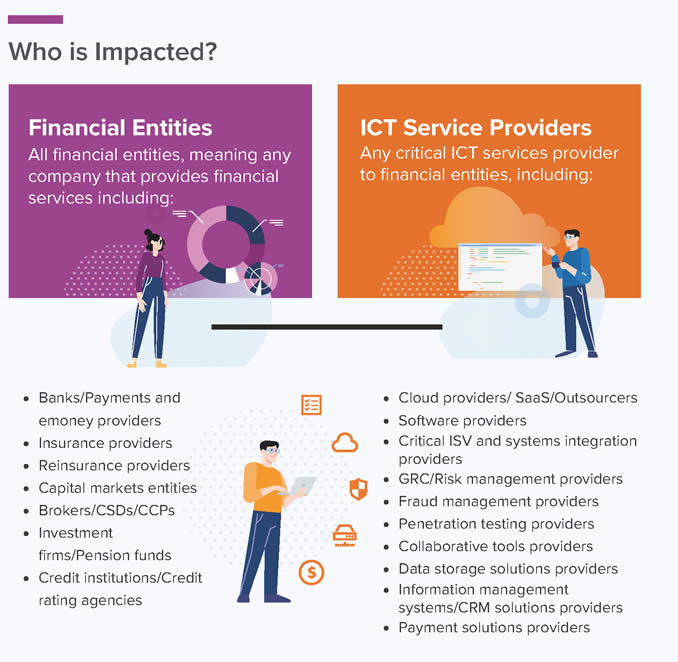
To this end, the ICT systems and networks of organizations operating within the EU financial sector must meet the uniform security requirements established by DORA. Such financial entities include banks, insurers, pension funds, credit institutions, and brokers, to name a few well-known ones.
DORA sets uniform requirements for the security of network and information systems of companies and organizations operating in the financial sector as well as critical third parties which provide ICT-related services to them, such as cloud platforms or data analytics services (Council of the EU)
In addition to all these financial entities, we also have the mentioned critical third-party ICT partners, which take different forms and shapes as ICT service providers for financial organizations. In our world of digitalization and tightly connected digital ecosystems, as we know it in finance and Fintech, some third parties are often almost inseparable partners rather than “simple” suppliers.
Examples of such third-party ICT partners include cloud services suppliers, software suppliers, system integrators, payment solution providers, companies that offer tools and services for cybersecurity and cyber risks, such as penetration testing, etc.
In short: an entire ecosystem whereby risk and security experts will undoubtedly see the many aspects of risk management (vendor risk management, supplier risk management, and third-party risk management in general). With DORA, third parties, such as critical cloud providers, obviously enter into the control of the proper designated supervisors and regulators.
The Digital Operational Resilience Act in a digital finance (regulation and guideline) context
So cybersecurity, cyber resilience, and in particular digital operational resilience, are at the heart of DORA, where the financial system’s vulnerability due to cyber threats and ICT disruptions is the challenge. It’s a familiar theme.
Indeed, as in other industries and services, this increasing vulnerability and the rise of cyberthreats and attacks are directly related to increased digitization and still-rising digital transformation in all areas, with growing digital footprints, software supply chains, and attack surfaces as a consequence.
Critical third-country ICT service providers to financial entities in the EU will be required to establish a subsidiary within the EU so that oversight can be properly implemented
And, of course, the more essential and critical ICT systems and infrastructure become, the more disruptive those ICT disruptions can be, especially in tightly interconnected environments.
This interconnectedness has multiple dimensions. First, it concerns the digitization and automation of numerous operations and processes. Whether it’s in connecting the back-office and front-end, in enabling digital and hybrid working, or to power ever more digital customer experiences: it’s an evolution that started years ago.
Next, there’s been – and still is – the emergence of digital-first processes and business innovations. And, connecting it all, there are the ever-growing digital interdependencies in the financial subsectors, with ecosystems, platforms, systems, and of course with those third parties and the new types of partners we’ve seen popping up in the finance industries.
These third parties primarily provide the necessary infrastructure and services in an increasingly tight financial ecosystem in which third-party risk management is naturally also becoming more critical. It is therefore evident that third-party risk management is one of the pillars of the Digital Operational Resilience Act.
With the regulation proposal, one of the financial services’ European supervisory authorities (EBA, ESMA, EIOPA) will have direct supervision over ICT service providers to enhance the overall financial industry’s digital resilience. – Maria Adele Di Comite (Research Director, IDC Financial Insights Corporate and Retail Banking)
As in other domains, the overall attack surface and vulnerable supply chain of third-party networks have grown significantly in the financial sector and the digital transformation of finance. And one can also refer to the accelerating role of the COVID crisis, in which we have seen a lot of rapid changes in banking and other financial services for users.
Research that we tackled before showed that the accelerating adoption of digital channels (for first-time use as well) during the first year of the pandemic was led by banking, while insurance followed in the eighth spot. Still, plenty of these evolutions in the sphere of digital finance started before; a matter of acceleration indeed.
The obligations of the Digital Operational Resilience Act require financial entities to take measures for the sound management of ICT third-party risk.
But that is certainly not all. The EU’s DORA is not isolated but forms part of a broader package of EU ‘digital finance’ measures. In addition to DORA itself, these also include, among others, a proposal regarding markets in crypto-assets (MiCA) and a proposal regarding distributed ledger technology.
Moreover, as the Digital Operational Resilience Act, DORA plays hand in hand with other digital-oriented EU legislative initiatives. Think especially of the GDPR or General Data Protection Regulation and the Network and Information Security Directive in this context of ICT and resilience. Others include e-IDAS and PSD2.
Furthermore, with the Digital Operational Resilience Act, not all is new. Since the financial sector is classically just about the most regulated in terms of cybersecurity and cyber resilience, there was already quite a lot of it, of course, on top of those larger regulatory frameworks.
An example is the Guidelines on ICT and security risk management, which the EBA (European Banking Authority) published in late 2019 and entered force in the Summer of 2020. Another example: the EBA’s revised Guidelines on outsourcing arrangement, also from 2019, in which it, among others, integrated its 2017 recommendation on outsourcing to cloud service providers and in which third-party risk strategies for ICT are required.
But there were also holes, and, at least as importantly, the EU wanted to harmonize and streamline everything much better and update and modernize. The latter is undoubtedly true if you look at the more holistic risk-based view strongly emphasized and the other regulatory initiatives the EU has in its ‘digital finance’ package.
The pillars of the Digital Operational Resilience Act at a glance
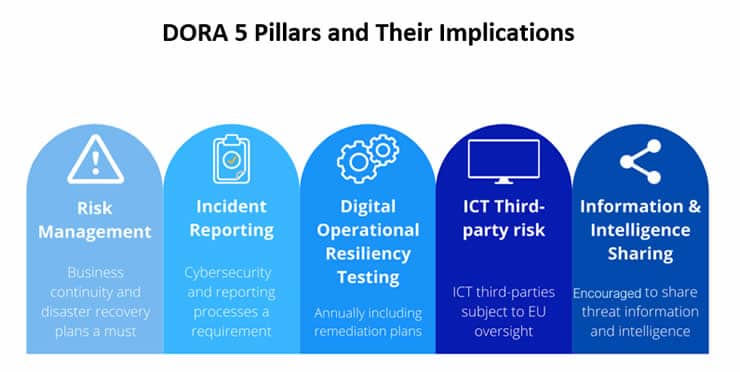
The Digital Operational Resilience Act is often viewed from four or five pillars with requirements for financial firms and their suppliers.
These are mentioned in the introduction to the proposal text. There is a sixth point, in Article 4, on governance, but it is never mentioned separately. The last topic, in Article 40, on information sharing, is also sometimes left out. We do briefly mention it here as a fifth pillar.
The increasing digitalization in the financial sector and the growing interconnectedness across financial institutions and third parties make financial institutions’ operations vulnerable to internal and external ICT and security risks that can potentially compromise their viability. As a result, sound ICT and security risk management are key for a financial institution to achieve its strategic, corporate, operational and reputational objectives. (EBA)
1. ICT Risk Management
The explanations and requirements regarding DORA’s section on ICT risk management can be found in Articles 5 through 14 of the Digital Operational Resilience Act proposal text.
In terms of ICT risk management, the text points out the need for functions in the various stages of ICT risk management: identification, protection and prevention, detection, response and recovery, training and development, and communication.
As mentioned above, harmonization and streamlining throughout various financial sectors is a focus or even a requirement here, whereby DORA, among others, builds upon the EBA guidelines.
For ICT risk management, the text effectively refers to existing standards. Furthermore, it emphasizes, among other things, the importance of the security and resilience of physical infrastructure and facilities that support the use of technology and the relevant ICT-related processes and people as part of the digital footprint of the financial organization. The various risk management elements should therefore include everything that has been outsourced to third parties.
2. ICT-related incident reporting
DORA also aims to harmonize and streamline the reporting of ICT-related incidents. The Digital Operational Resilience Act refers to the general obligation to establish a management process within financial entities and the rules for monitoring, recording, classifying, and reporting ICT-related incidents.
In time, as part of the harmonization, the purpose is to have a hub within the EU for reporting ICT-related incidents by financial entities. That would be welcome since today there are many rules and regulations and reporting mechanisms and bodies. Just think of the GDPR and the previously mentioned Network and Information Security Directive or NIS (for which there is a replacement, “NIS2”) but also of e-IDAS, PSD2, the Single Supervisory Mechanism (SSM), and so on.
3. Testing digital operational resilience
In cybersecurity, cyber resilience and achieving compliance with all these regulations, monitoring, and testing are indispensable.
It is the same in the Digital Operational Resilience Act or DORA. So, there is a pillar of testing for digital operational resilience (in Articles 21 to 24) that defines the testing requirements as a function of the size and risk profile of the organization or entity, the tools, and more.
The digital operational resilience testing programme shall provide for the execution of a full range of appropriate tests, including vulnerability assessments and scans, open source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing or penetration testing (Article 22, DORA)
For the latter, there are still some details to be worked out in the future, and there are some specific rules on penetration testing, one of the many ways to test resilience, security, and preparedness.
It goes without saying that testing alone is not enough and that taking corrective action according to the results is also essential.
4. ICT third-party risk
We already discussed this pillar in more detail at the beginning. With the harmonized introduction of ICT third-party risk, the EU is bringing quite a few third parties into the new streamlined supervisory framework for the financial sector.
They all provide services in a digital and ICT context, but it is a relatively large and broad ecosystem of organizations. Just think of all the types of financial entities and then all the types of ICT services, products, digital connections, and so on that they have/need with a range of third parties providing them. Not that third-party risk management in the financial sector is new, of course. Moreover, it is also built on previously mentioned EBA outsourcing guidelines.
The regulation is designed to ensure a sound monitoring of ICT third-party risk. This objective will be achieved first through the respect of principle-based rules applying to financial entities’ monitoring of risk arising through ICT third-party providers (Proposal text)
And it goes remarkably far. ICT third parties will fall under the direct authority of the authority that will take care of the overview. And there is more, including in terms of the countries in which the third party is based. For DORA, ICT third-party risk is also managed as an integral part of the ICT risk management framework. Again, it indicates the growing importance of third-party risk management or TPRM, not only in the financial sector—more on the ICT third-party risk pillar in articles 25 to 39.
5. Information sharing
Last but not least, there is the pillar of information sharing that you can read about in Article 40 of the text, as mentioned before.
The cyber threat information and intelligence sharing arrangements drive the mutual sharing of such information between financial entities to the extent that it is done within communities of trust and to strengthen the digital operational resilience of the financial entities.

