The rapid and continuous expansion of organizations’ attack surface and digital footprint has led to (external) attack surface management being one of the most important cybersecurity trends.
Attack surface management (ASM) is hot. In fact, several factors are not only contributing to the expansion of organizations’ attack surfaces but simultaneously ensuring that attack surface monitoring and management will continue to grow strongly for several more years.

Some of these factors have been in place for several years. Think, among others, of digital transformation, the changing IT vision and approach, digital ecosystems, decentralization of IT, shadow IT, cloud computing, remote and hybrid work, the future of work evolution, and the Internet of Things. This small list is far from exhaustive.
Other factors driving the growth of organizations’ digital footprint, attack surface, and – as a result – need to manage it all are directly related to evolutions during the COVID-19 pandemic and/or to developments regarding cyberattacks and cybercrime with the increase of software supply chain attacks being one.
The attack surface and what managing it means
We begin with a brief overview of the attack surface and why monitoring and managing it matters.
Next, we take a quick look at how ‘new’ cybersecurity technologies and terms such as External Attack Surface Management (EASM) and Cyber Asset Attack Surface Management (CAASM) fit in. We also very briefly explore their relationship with other security domains.
The increased complexity of environments and expansion beyond what used to be a defined perimeter has many searching for solutions that help security teams understand and manage their entire attack surface (Michelle Abraham, research director, Security and Trust at IDC)
In terms of terminology, we need to distinguish between different cyber security vendors and analysts specialized in IT and security. For instance, only a few of the latter use the term external attack surface management, while others utilize attack surface management. Sometimes, you will see that synonyms are employed whereby not everyone is equally consistent, both for attack surface and attack surface management.
The term attack surface initially referred to the total of all vulnerabilities and access points of a system, application, or network accessible and usable by hackers. NIST defines the attack surface as follows: “The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment.”
We often see that it depends heavily on individual IT and security practitioners which classes or categories of IT assets they do or do not include in the ‘notion’ or definition of the attack surface.
The IT assets that are considered part of the attack surface expanded as time went by, and we started using “new” types of connected assets, code, systems, and so forth. The IT world is very dynamic. So it is not only about who defines the term but when the definition you stumble upon was written that matters. The concept of the attack surface – whereby people initially often focused on the need to keep it as small as possible and the measurement of the surface – is not that new.
An attack surface is the total number of points/vectors through which an attacker could try to enter your IT environment (Brad LaPorte)
An example of assets that some today include under ASM are IoT devices that, for the time being, however, are less used and thus less top of mind as part of the enterprise attack surface, compared to, for example, assets and workloads in the cloud. But once you have an IoT (Internet of Things) project in production, it is already harder to overlook those devices as parts of your overall attack surface. So the term evolves, and not everyone understands it the same way.
We also see that everything related to third and even fourth parties (think of third-party risk management, supplier risk management, vendor risk management, and software supply chains) is increasingly included in the attack surface.
To summarize, the definitions and descriptions vary depending on the period in which they have been drafted, as the underlying reality is constantly evolving. Reality is dynamic, and digital business reality is even more so. Whatever the case may be, the enterprise attack surface is getting larger. And that, of course, is important to the aspect of management and certainly not just a matter of a wider pallet of asset types and the increase in internet-facing assets.
Research firm Gartner placed attack surface expansion at the forefront of its Top Security and Risk Management Trends list for 2022, which it announced in March 2022.
In this context of the expanding attack surface and the increasing importance of attack surface management, the company, among others, also pointed to the risks associated with more factors that have pushed organizations’ exposed surfaces beyond a set of controllable assets. Gartner, for instance, cites the use of cyber-physical systems (e.g., Industry 4.0) and IoT, open-source code, cloud applications, complex digital supply chains, and social media.
So many security and IT teams struggle to maintain much-needed visibility into an increasingly complex and distributed IT environment because so much of an organization’s estate is unknown or undiscovered due to shadow IT, M&A, and third party/partner activity (Jess Burn, Senior Analyst, Forrester)
EASM and CAASM
Gartner has introduced two new terms in attack surface management in recent years: the previously mentioned External Attack Surface Management (EASM) and Cyber Asset Attack Surface Management (CAASM), referring to new categories of products/solutions per Gartner. They also appear in the Gartner Hype Cycle for Security Operations at the beginning of the ‘innovation trigger’ stage.
Gartner calls EASM an essential new technology (category) in cybersecurity in its Hype Cycle for Security Operations 2021 report, which is offered for download by the EASM vendors mentioned in the report.
Gartner defines EASM as “an emerging product set that supports organizations in identifying risks coming from internet-facing assets and systems that they may be unaware of.”
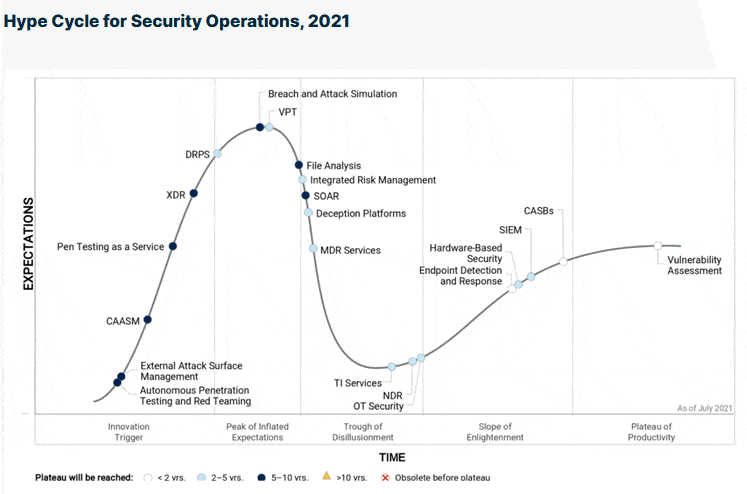
Former Gartner research analyst Brad LaPorte describes in a blog post how attack surface management (without the ‘external’) was initially defined as “the processes, technology and professional services deployed to discover external-facing enterprise assets and systems that may present vulnerabilities. Examples include servers, credentials, public cloud service misconfigurations, and third-party partner software code vulnerabilities that malicious actors could exploit”.
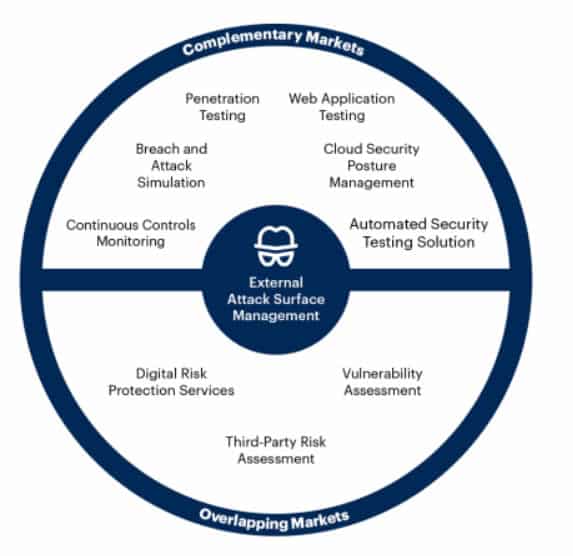
External Attack Surface Management overlaps with other security domains, such as the already mentioned third-party risk assessment (TPRM), vulnerability assessment, and digital risk protection services.
In addition to overlapping markets, there are complimentary ones such as pentesting (penetration testing), cloud security posture management (CSPM), and more.
External Attack Surface Management is an emerging concept that is growing quickly in terms of awareness within the security vendor community but at a slower pace within end-user organizations (Gartner)
The graphic from Gartner below clearly shows how EASM, which is expected to “become part of a broader vulnerability and threat management push aimed at discovering and managing internal- and external-facing assets and potential vulnerabilities”, overlaps with some existing markets and is complementary to others.
As the people of Sweepatic, named by Gartner on its 2021 Emerging Vendors list in the external attack surface management security category, who posted the graphic here, state one of the key findings of Gartner’s report is that external attack surface management (EASM) capabilities cross over into other existing security markets like digital risk protection services (DRPS).
The external view in trying to manage the total attack surface
Other analysts, such as Forrester and ESG, talk about ASM when they mean external attack surface management as well. Forrester defines attack surface management as follows: “The process of continuously discovering, identifying, inventorying, and assessing the exposures of an entity’s IT asset estate.”
This is also the definition most often found by vendors. Some of the latter also use terms like digital footprint monitoring, digital risk monitoring, and external attack surface monitoring. In addition, monitoring’ and ‘management’ are often used interchangeably in the context of ASM and similar terms.
By focusing on the ‘external’ aspect in EXTERNAL attack surface management, Gartner draws attention to the increase of external cyber threats across an ever-broadening landscape of all sorts of ecosystems and technology layers with complex supply chains. Therefore, it should not be surprising that we look more often from an outside-in perspective in a holistic cybersecurity approach, as is the case with (E)ASM.
ASM is an approach to the security of your digital footprint from the perspective of threat actors.
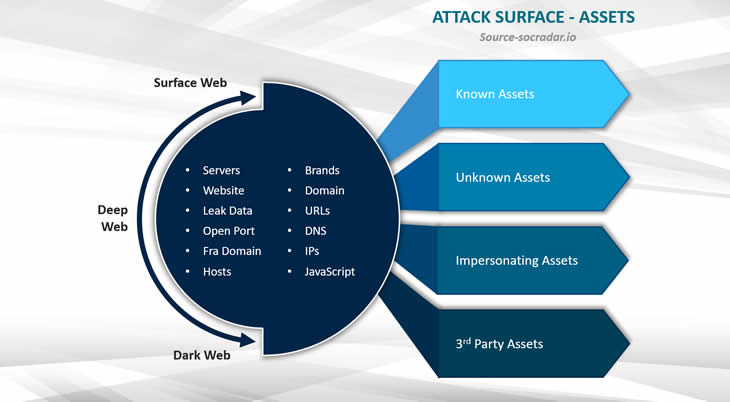
Or, perhaps better, an external view. And one of the most often mentioned aspects regarding attack surface management is that it helps organizations see the entire attack surface thanks to this external view. And that typically includes assets companies didn’t even know they had in this increasingly complex digital world. It’s what nearly all vendors and their clients will tell you.
As IDC puts it, “attack surface management, with its external view of the organization, can surface vulnerabilities in systems the organization did not know existed.”
To quote Michelle Abraham, research director, Security and Trust at IDC: “The increased complexity of environments and expansion beyond what used to be a defined perimeter has many searching for solutions that help security teams understand and manage their entire attack surface.”
That’s what ASM is about to improve security and risk posture and, thus, as Michelle reminds us, improve trust.
One challenge is to have that full attack surface view (and the insights to improve it) by using the right tools. In that context, remember that the attack surface can encompass many elements but isn’t the same for everyone, which goes for the offering of vendors as well. Yet perhaps you don’t need everything; it all depends on choices, risks, and what is most important here and now first.
Attack surface management – a market in flux for a dynamic and complex reality
The relatively young market of External Attack Surface Management solution providers is in full flux.
Emerging vendors like the previously mentioned Sweepatic and many others, such as SOCRadar, Reposify, CyCognito, and FireCompass, expand their capabilities and find their approach, often based on their historical focus.
Unfortunately, some vendors offer more limited security and digital footprint scanning and monitoring tools but start rebranding what they do without being comparable to EASM vendors.
43 percent of IT and business leaders state that the attack surface is spiraling out of control. 73 percent are concerned with the size of their digital attack surface.
Yet, the large cybersecurity platform providers can’t be absent either. Moreover, since customers increasingly want a single actionable view instead of large stacks with different security solutions, with Gartner expecting further integration and consolidation in the market, they all position themselves along those lines.
Trend Micro, for instance, launched its Trend Micro One technology ecosystem in 2022 with an inaugural partner active in external attack surface management: Bit Discovery. Since then, it was acquired by another inaugural partner, Tenable, and is called Tenable.asm (with the .asm indeed standing for Attack Surface Management).
Research by Trend Micro, which we briefly mentioned in an article on the company’s report on why global organizations struggle to manage cyber risk, also looked at the evolution of the ‘digital attack surface’ challenge.
Per Trend Micro, 43 percent of IT and business leaders state that the attack surface is spiraling out of control, and nearly three-quarters (73 percent) are concerned with the size of their digital attack surface.
The digital attack surface is the collection of applications, websites, accounts, cloud infrastructure, on-premises servers, operational technology (OT) and other elements which are often exposed to remote threat actors (Trend Micro).
In the meantime, the visibility challenges of the attack surface continue to grow as threat actors deploy a range of tactics, techniques, and procedures (TTPs) to target various corporate attack surface elements.

