Cybersecurity is the protection of IT systems and assets, their users, and other potential victims of cyberattacks and cyber incidents.
Cybersecurity requires a risk-oriented approach whereby identified cyber risks, continuous monitoring of vulnerabilities across the supply chain, and (data) protection priorities drive a holistic security strategy.

There are several definitions of cybersecurity, and many of them have evolved, just as the role, nature, threats, and perceptions of cyberspace, IT systems, and the digital economy have changed.
In various cybersecurity definitions, the authors tend to elaborate a bit more on the multiple systems and (classes of) assets to be protected, the role of people, the types, nature, and purpose of threats, and other functions than the sheer act of protecting. To protect, one has to know what needs protecting (and how) and what to do when breaches or attacks occur too obviously.
Cyber risks and cybersecurity in flux: a holistic business approach
Cybersecurity is not only a practice but also a knowledge domain, strategic activity, and a growing set of initiatives and practices by various organizations, whereby some have taken the form of guidelines or even frameworks to help organizations benefit from lessons learned. Such models, frameworks, and standards also facilitate the development of a cybersecurity strategy and can help make you more cyber resilient.
The purpose of a security program is not to ensure we don’t get hacked; that’s an impossible goal. The purpose of a security program is to balance the needs to protect with the needs to run the business. (Paul Proctor at the Gartner Security & Risk Management Summit 2021 Americas)
Cybersecurity goes beyond a reactive and protective approach and looks at pro-active means of protection and includes the steps to take if protection turns out insufficient and hacks/breaches occur (response, mitigation/recovery, etc.).
One of the better-known cybersecurity frameworks, the NIST (National Institute of Standards and Technology) Cybersecurity Framework, for instance, includes five cybersecurity functions in its core. According to NIST, they represent the five key pillars of a successful and holistic cybersecurity program.
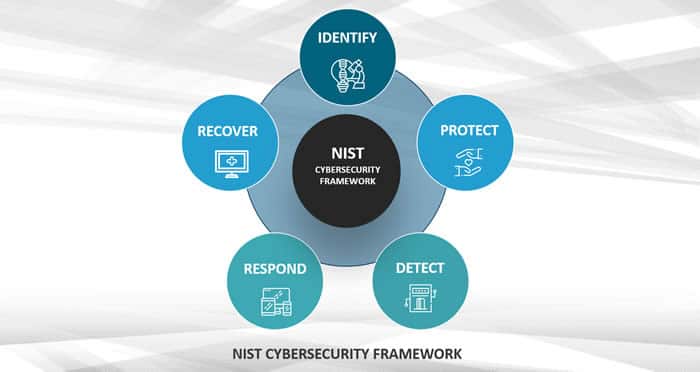
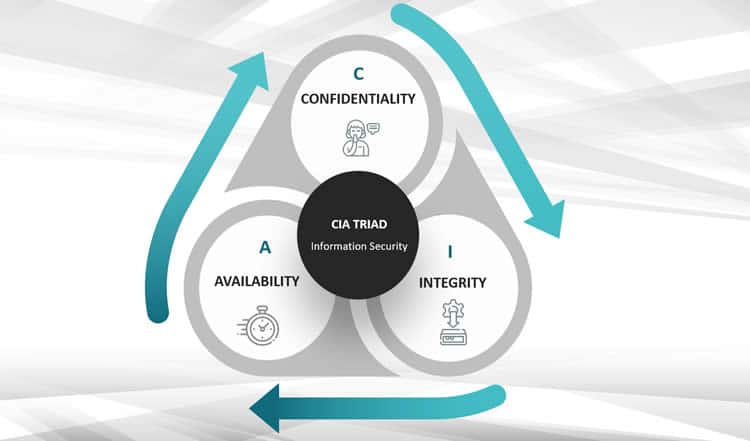
You’ll notice how the ‘recover function’ is also about implementing improvements based on what has been learned. The ‘identify function’ also requires identifying a risk management strategy and governance program. In other words: it goes beyond good old tactics to ensure confidentiality, integrity, and availability (the so-called CIA Triad of information security, see below).
We have to change the way we think about security. A lot of the disruption and cost is due to a focus on prevention as opposed to detection (Dr. Ben Azvine, Global Head of Security Research and Innovation at BT)
The five key pillars (functions) of the NIST cybersecurity framework core:
- Identify: the Identify Function assists in developing an organizational understanding of managing cybersecurity risk to systems, people, assets, data, and capabilities.
- Protect: the Protect Function supports the ability to limit or contain the impact of potential cybersecurity events and outlines safeguards for delivering critical services.
- Detect: the Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event on time.
- Respond: the Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident to minimize impact.
- Recover: the Recover Function identifies appropriate activities to maintain resilience plans and restore services impaired during cybersecurity incidents.
Finally, our views (definitions, frameworks, etc.) regarding cyber security reflect the evolving views on cyber risks, emerging threats, and how we (can) deal with them. Especially in recent years, a lot has changed regarding cybersecurity and risks.
With regards to these changes, among others, consider:
- the rise of third platform technologies (e.g., cloud computing, mobile, big data),
- the importance and speed of digital transformation and digital business,
- the role of digital connectivity and systems across all areas of life, business, and our built environment,
- the accelerating adoption of digital technologies by organizations and individuals throughout recent crises that increases our dependence on technology even more,
- the increasing number and complexity of cyberattacks, and
- the meeting of digital and physical spaces and assets, including the cyber-physical systems of Industry 4.0 and the rise of the Internet of Things.
Cybersecurity concerns represent the biggest perceived risk to successful digital transformation, especially since it seems hard for organizations to find a common language, enabling to take appropriate and risk-based actions.
On a deeper level, the extended enterprise, data-sharing practices, and digital ecosystems, combined with a decentralized business approach, have also seriously impacted cybersecurity.
Decentralization –for instance, in how we work and structure our IT environments now – is enabled by ubiquitous connections, resulting in larger digital footprints and attack surfaces that offer cybercriminals new opportunities (and mean more emerging risks for organizations). A more elaborate list of recent evolutions affecting the field and the importance of cybersecurity, including decentralization’s impact, is coming soon.
Cybersecurity is the set of security measures taken to prevent, mitigate and recover from damage caused by a failure, outage, or misuse of an information system, computer, or online asset.
Cybersecurity definitions: various views on what cybersecurity is and means
Below are some “official definitions” of cybersecurity.
Cybersecurity definitions by NIST (National Institute of Standards and Technology, US):
“The ability to protect or defend the use of cyberspace from cyber attacks.” “Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation.”
Cybersecurity definition in Regulation (EU) 2019/881 on ENISA (European Union Agency for Cybersecurity) and on information and communications technology cybersecurity certification:
“Cybersecurity means the activities necessary to protect network and information systems, the users of such systems, and other persons affected by cyber threats.”
Cybersecurity definition by Gartner (research firm): “Cybersecurity is the combination of people, policies, processes, and technologies employed by an enterprise to protect its cyber assets. Cybersecurity is optimized to levels that business leaders define, balancing the resources required with usability/manageability and the amount of risk offset.”
Cybersecurity definition by the ITU (International Telecommunication Union) in Recommendation ITU-T X.1205:
“Cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance, and technologies that can be used to protect the cyber environment and organization and user’s assets.”
Cybersecurity definition by the CISA (Cybersecurity and Infrastructure Security Agency, US):
“Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information.”
In the context of our articles on cybersecurity, we mainly look at the practice of cybersecurity, its importance, the various threats, and the trends that organizations need to be aware of to protect their organization optimally, digital ecosystems, and (networks of) people – with a strong focus on risk management.
The traditional security perimeter has dissolved. With new technologies come new possibilities and new risks. As a result, organizations must master the changing cyber threat landscape, protecting data and applications in this new perimeter-less world.
Evolving cybersecurity visions
The changing reality of cybersecurity has continuously led to various models where new visions and models had to make up for the shortcomings of the previous ones or were better adapted to this ‘new’ reality.
Moreover, there have been and are advancing insights in cyber security: fighting cyber attacks and making organizations cyber resilient from a risk perspective is a dynamic reality that is never finished.
Yet it is primarily the increasing complexity of our IT environments and digital ecosystems and the increasingly complex ways in which attacks are prepared and executed that are causing changes in terms of visions and strategies.
Several factors, some of which we mentioned earlier, have significantly changed the risk profiles of companies. Think of all the new technologies and their impact on our security strategies, the accelerating digitalization, and the expansion of the attack surface whereby ever new cybersecurity layers and defense mechanisms had to be fitted into an increasingly complex puzzle. For adversaries, it led to new entry routes that, in turn, created risks we hadn’t encountered and called for new approaches.
The traditional security perimeter has dissolved. Cloud computing, mobile devices, big data analytics, AI, and emerging technologies have the potential to make organizations more efficient, but they also introduce new risks. And it’s not just about all the technologies but about how we leverage them to create and/or join connected ecosystems where all the technology, in the end, gets seen as a commodity by people using it.
The border between the “secure” internal network that needed to be defended like a castle and the evil outside world is gone. What is “internal,” and what is “external” today? Of course, such a view of two separate worlds or the old castle-and-moat model was always an overly simplistic vision. That secure network was never completely secure except in theory. Consider, for example, the human factor. In the decentralized world of cloud and digital transformation, connecting to that outside world has also become more the rule than the exception, with more and more connections and a larger attack surface.
The technological boundaries are blurring, as are the boundaries of our business. The good old perimeter is, in practice, nowhere. And, at the same time, everywhere. And we have replaced the old castle-and-moat model with zero trust and other approaches. But more on that later.
The World Economic Forum estimates a gap of more than 3 million cyberSecurity experts worldwide.
What are cybersecurity and threat frameworks and models?
Cybersecurity is at least as much a matter of policies, practices, people, processes, and frameworks (sets of standards and procedures) as it is about technologies and tools.
Cybersecurity and related concepts such as information security and IT security only became important and broadly covered at the end of the previous Millennium.
The success of personal computers, the advent of local area networks, and, last but not least, the rise of the Internet (with the WorldWide Web and the general use of email) were among the factors leading to the increase of malware and cyber threats in the 1990s.
For a few decades, the main cybersecurity challenges, types of cyber threats, and ways to deal with them remained more or less the same.
However, the arrival and rising success of several so-called third platform technologies and accelerators brought a range of new risks, further driven by the rapidly growing importance of digital technologies for business and the economy alike, with data at the core of changing paradigms.
For a long time, the principal security model remained the so-called “CIA Triad,” which we have known since the seventies: Confidentiality, Integrity, and Availability as the primary – interconnected – goals of (information) security.
Today, we use increasingly sophisticated cybersecurity frameworks as security and threats have become far more complicated, and our digital environment keeps rapidly expanding, although the essence remains the same. Moreover, given the importance of cybersecurity and data protection, several standards and regulatory frameworks have seen the light of day in recent years.
Next, we’ll tackle some of all those cybersecurity views, models, frameworks, and standards you might encounter, even if some are perhaps outdated.
More articles on cybersecurity and related topics:
Below is a list with more articles on cybersecurity, cyber resilience and related topics.
- CNAPP adoption: Cloud Native Application Protection Platform drivers
- The role of the Chief Supply Chain Officer in TPRM and cyber resilience
- SaaS security in an expanding reality of third-party connected apps
- The state and future of phishing in a complex world and age
- IT security spending patterns and priorities Europe 2022-2026
- The attack surface and importance of attack surface management
- The record-breaking average cost of a data breach in 2022
- What is TPRM? Third-party risk management and cyber risks
- Why cyber risk (exposure) is increasingly challenging to manage
- CISOs and CROs underestimate cyberthreats from digital ecosystems
- The state and challenges of OT cybersecurity 2022
- Security and risk management as an inherent part of business
- Penetration testing in an increasingly complex digital world
- The MITRE ATT&CK framework and evaluations explained
- The ransomware readiness gap and mitigation strategy challenge
- Software supply chain security: state and outlook
- The EU’s DORA Digital Operational Resilience Act for digital finance
- Splunk: top security issues facing the enterprise in 2022
- The state of cloud data security: challenges and recommendations
- MITRE ATT&CK for ICS shines light on industrial attack tactics
- OT and ICS security – the human dimension and organizational challenges
- Cyber resilience: business continuity and cyber incidents

