Reporting on Industry 4.0, digital transformation, Internet of Things, cybersecurity, AI and emerging technologies.
Succeed in connecting the dots between digital business, transformation, processes, value, & purpose.
Industry 4.0 is the digital transformation of manufacturing/production and related industries and value creation processes. Industry 4.0 is used interchangeably with the fourth industrial…
- Tom Cuylaerts
The technologies that are typically associated with Industry 4.0 and digital transformation in manufacturing probably need no more introduction: cloud computing, (big) data, the…
- Tom Cuylaerts
TQM stands for Total Quality Management. It is
- Tom Cuylaerts
According to a report, 34 percent of enterprises
- Tom Cuylaerts
The term Industry 5.0 popped up several years
- J-P De Clerck
Smart manufacturing has been defined as the fully-integrated,
- Tom Cuylaerts
Despite geopolitical and macroeconomic uncertainties, the projected global technology and IT spending for 2025 shows an acceleration compared to 2024. The digital economy will…
- J-P De Clerck
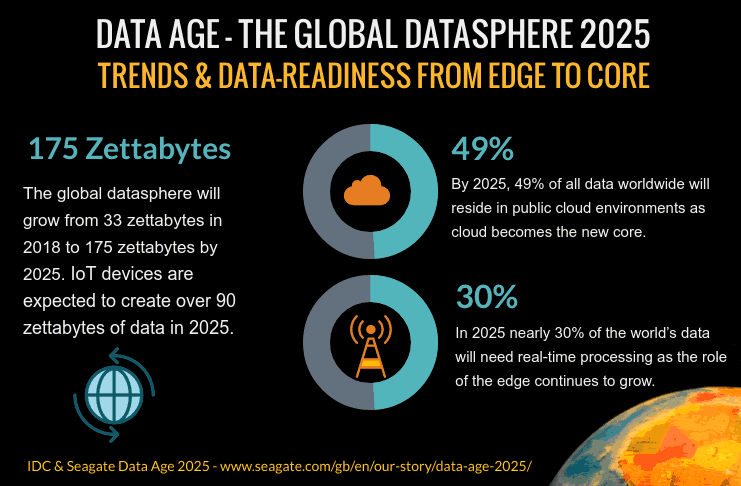
A look at Data Age 2025, a collaboration
- J-P De Clerck
Digital transformation requires a digital transformation strategy that,
- J-P De Clerck
What is big data, how is it used,
- J-P De Clerck
Digitization, digitalization and digital transformation are three terms
- J-P De Clerck
In today’s connected economy, we work with an increasing number of third parties. And every time we onboard another third party, we open ourselves…
- Tom Cuylaerts
The rapid and continuous expansion of organizations’ attack
- Tom Cuylaerts
Confidentiality, integrity, and availability are known as the
- J-P De Clerck
An introduction to and definition of cyber resilience,
- J-P De Clerck
Cybercrime and cyberattacks continue to rise with ever
- J-P De Clerck
A look at IoT technology and the first layers of the IoT technology stack: endpoints and devices (including sensors and actuators), IoT gateways (and…
- Tom Cuylaerts
Sensors have become ubiquitous. They have existed since
- Tom Cuylaerts
For several years, organizations started transforming their offices
- J-P De Clerck
The Internet of Everything (IoE) is a concept
- J-P De Clerck
Guide to Industrial IoT (the Industrial Internet of
Artificial intelligence
- Tom Cuylaerts
- Tom Cuylaerts
- Tom Cuylaerts
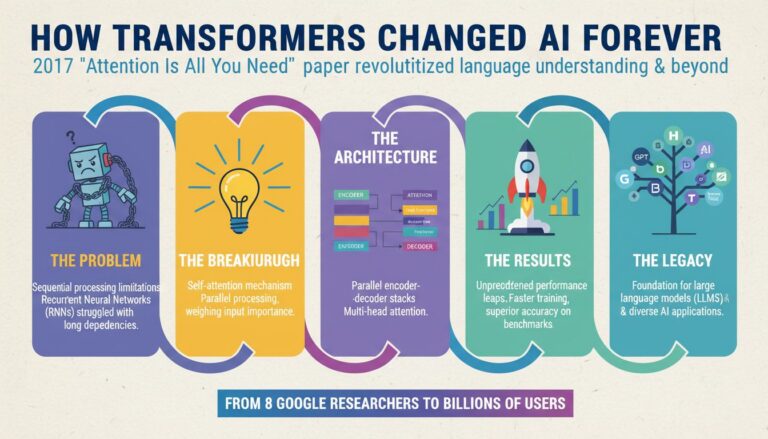
DeepSeek V4 represents a significant leap forward for
- Tom Cuylaerts