Security and the Internet of Things: looking at challenges, solutions and the need for a security by design approach in IoT business plans.
The Internet of Things is not just generating a tsunami of data for which new connectivity and data analysis approaches are developed, such as fog computing (think cloud computing meets edge computing) and others.
The IoT is also generating a tsunami of risks and concerns in the areas of Internet of Things security, regulatory compliancy and data privacy. Security experts have warned that the Internet of Things is a cybersecurity nightmare and it’s only a matter of time before a large scale attack is unleashed, using IoT vulnerabilities.
Such large scale attacks, using connected devices and the IoT, have already happened as you know.
The Internet of Things in consumer applications: privacy, compliance and threats
It has caused the industry to step up the pace and sound the alarm bells even more. And, as is the case when something goes wrong, the finger pointing started. But it’s good that these discussions take place, especially as the fear for even bigger attacks (whether it’s DDoS, ransomware or others) is real, the IoT is real too and it is becoming ever more important.
Privacy and compliance in the IOT
On top of the pure security aspect, there are the privacy and regulatory aspects. All three are connected, especially as quite some new regulations concern the usage of private data and as compliancy is one of the key drivers in the security industry today.
The data privacy dimension is more (but not solely) related with the Internet of Things in a consumer context and it needs to be taken serious as it’s one of the reasons why there still is hesitance regarding consumer applications in the IoT space, such as wearables or smart home automation and even regarding more hybrid consumer/industry applications, such as or smart meters. And of course consumers also deserve secured environments in which their data are protected. Why else pay for them?
Consumer IoT security challenges and perceptions
Consumers are also wary about the security aspect of the IoT: when Accenture noted there is a gap to bridge in the consumer electronics market where amidst declining growth, the industry awaits a boost from the IoT in consumer electronics, security was mentioned as a clear challenge to address.
As in the eyes of consumers, the Internet of Things is “a thing”, there is certainly an impact of all the media attention for breaches whereby the IoT is used as a weapon by the “bad guys”.

When the highly popular website of security journalist Brian Krebs was attacked by a huge IoT Distributed Denial of Service attack end September 2016, causing the website to go down (the DDoS attack went up to 620 Gbps or gigabits per second), a Belgian newspaper wrote an article (in Dutch), entitled “Heaviest cyber attacks ever: someone is testing how to bring down the Internet”, refering to among others ‘the Krebs attack’.
The article clearly mentioned the dangers and potential exploitation of connected devices and the IoT by hackers as did many other media across the globe, from mainstream to specialized. And that is what consumers see and remember: the headlines and the fears.
Key Internet of Things security challenges
One of the most prolific and outspoken security gurus in the matter, whom we mentioned in our article on the need for an open cybersecurity debate in the DX economy, is Bruce Schneier.
In an article on Computing he says it’s not just internet-connected electronic voting systems that will be targeted by foreign powers (another hot topic lately). Schneier even warns us over ‘IoT-geddon’ (registration required to read).
Integrity, availability and the patch issue
In a blog post, Schneier describes the security challenges regarding the Internet of Things from the traditional CIA view.
We don’t mean the agency but the well-known security acronym CIA, which stands for Confidentiality, Integrity, and Availability. In the post, Schneier explains why on the Internet of Things integrity and availability threats are far worse than confidentiality threats.
In an older ‘essay’, Schneier describes the security challenges regarding embedded systems and the IoT whereby devices (and embedded computers) are “riddled with vulnerabilities”. Moreover, there is no good way to patch them.
That’s also what the Chief Security Officer (CSO) of Akamai, Andy Ellis, said end September 2016 to The Register, urging for a culture change in IoT architecture whereby a big piece of the challenges is the difficulty to patch IoT devices and thus to update them with vulnerability and security updates.
Akamai offers Content Delivery Network (CDN) and Cloud Computing Services. It also is the company that provided anti-DDoS services (for free) for Brian Krebs’ website but had to stop because of the scale and impact of the attack (Kreb’s website was then added to Google’s DDoS attack mitigation service Project Shield).
So, patches are part of the problem and, more importantly, the difficult upgrade process for most of today’s IoT devices as Akamai’s CSO explains it in the mentioned article on The Register.
A cascade of IoT security vulnerabilities
What are the other challenges? Back to Bruce Schneier: on top of unpatched systems and the issue of software control there are challenges regarding the:
- By definition highly interconnected nature of the Internet of Things. To use Cisco’s term, in the Internet of Everything where we connect devices, processes, people and data, vulnerabilities in one device can lead to a cascade, involving several other devices.
- Automation and the degree of autonomy. Schneier warns about the ability of devices (or the software they contain) to take autonomous decisions without human control which also brings us to a larger context of automation and even artificial intelligence.
You can read the full article here.
The growth of advanced security threats
One of the reasons we mention Schneier is because of that earlier mentioned article in a Belgian newspaper where the author sums up other IoT DDoS attacks and refers to another article of Schneier in the context of the broader statement that someone is testing how to bring down the Internet.
Schneier published the post one month before the ‘Krebs case’, it is entitled “Someone Is Learning How to Take Down the Internet”, and it points the finger of probable origins to state-sponsored efforts using DDoS and vulnerable pieces of the Internet (and that includes devices).
While some find the article too vague and didn’t talk about the IoT in specific it shows how mainstream media add to doom scenarios. Are these scenarios correct? Many do agree with Schneier and say it’s not a case of ‘if’ but of ‘when’.
What’s for sure is that the capabilities, both regarding technology and organization, of hackers certainly went up.
Advanced threats are growing fast and according to Zscaler, a provider of security in the cloud, close to 60 percent of these advanced threats come in over encrypted traffic as Zscaler’s Chief Information Security Officer (CISO), Chris Hodson told us in an interview we conducted for the BT Let’s Talk blog.
IoT security: looking at solutions
Back to security in a context of the Internet of Things.
It’s of course also a topic security journalist Bryan Krebs reports on as in his post “IoT Reality: Smart Devices, Dumb Defaults” (by the way: the attack on his website, using cameras and IoT devices, was conducted by a few hackers as a way of revenge regarding some posts he wrote and which exposed a group of hackers for hire).
But what are the solutions? Can the Internet of Things be secured? There is certainly a lot that can be done as you’ve already discovered in this article. And it’s of course critical to do what can be done. But it will happen in a gradual way. Maybe we need more awareness to move from gradual to exponential?
More awareness
Unfortunately growing attention and action to solve something often occurs when that something went bad. In the aftermath of the ‘Krebs attack’ a bunch of opinion pieces and articles appeared regarding the Internet of Things and security. It’s clear that the attack on Krebsonsecurity.com has created a momentum to move faster in regards to improving security of the IoT.
A critical step is creating awareness about the issue. That’s certainly what people like Schneier, Krebs and, probably unwillingly, hackers do. It’s also what a gazillion of security experts, security service providers, researchers and analysts have been doing for many years.
The role of the boardroom
However, awareness is not enough. There needs to be a mandate coming from the boardroom, where CSOs, CISOs, CIOs and data experts should get a place around the table (and increasingly do get one) and where the money and message needs to come from, to embed security everywhere, steer away from developing new solutions with a mindset of just maximal profit (leaving investments in key security controls out), go for security by design and not just talk the talk but also walk the walk when it boils down to mitigating the risks of that key business asset, called data, which in the end, along with process automation, is what the Internet of Things is all about.
This boardroom aspect is also mentioned in another article on The Register, covering an event where the IoT and security/privacy issue was tackled, again with the ‘Krebs case’ in mind.
Two quotes:
- “Educate boardroom and senior management to build security in from the start.”
- “The success of the IoT will come down to users’ confidence.”
Holistic approaches for the ubquituous perimeter
Another important element to mention is the need for a holistic security perspective whereby the perimeter is really ubiquituous.
It’s not just about endpoints, changing or fading perimeters, mobile users and cloud: the new security perimeter is the perimeter of everything (with a prioritized approach).
Pro-activity matters as well in this perspective as does the need to monitor for evolving challenges. Few companies are able to do all that by themselves so finding the right partners is key here.
Among the latest evolutions in the area of the Internet of Things is, for instance, the move of ransomware (the number one security challenge at this moment) towards the Internet of Things. In other words: soon everything can potentially be held for ransom, including devices and IoT applications. And regulators know it.
The Internet of Things and regulation: GDPR, ePrivacy and moreWhat the analysts say: predictions on IoT security
To conclude here are some predictions and quotes from a few analysts on the Internet of Things and security (we mentioned two in a shortened version earlier).
- “What CIOs should pay attention to instead is the fact that IoT will drive concrete change inside their companies in critical areas like data management…, financial reporting, business metrics, security, and systems architecture.”.
Source: How The Internet Of Things Will Challenge CIOs To Evolve How Their Firms Operate And Engage With Customers (Forrester). - “Through 2018, over 50% of IoT device manufacturers will not be able to address threats from weak authentication practices.”
Source: Gartner’s Top 10 Security Predictions 2016 (June 15, 2016). - By 2020, 10% of All Attacks Will Target Intelligent IoT Systems.
Source: IDC FutureScape: Worldwide Internet of Things 2016 Predictions. - “Two-thirds of enterprises will suffer IOT security breaches by 2018.”
Source: ITBusiness.ca (quoting Frank Gens, IDC). - “By 2020, more than 25% of identified enterprise attacks will involve IoT, though IoT will account for only 10% of IT security budgets.”
Source: Gartner’s Top 10 Security Predictions 2016 (June 15, 2016).
Convincing the boardroom: IoT security is an intrinsic part of an IoT business plan
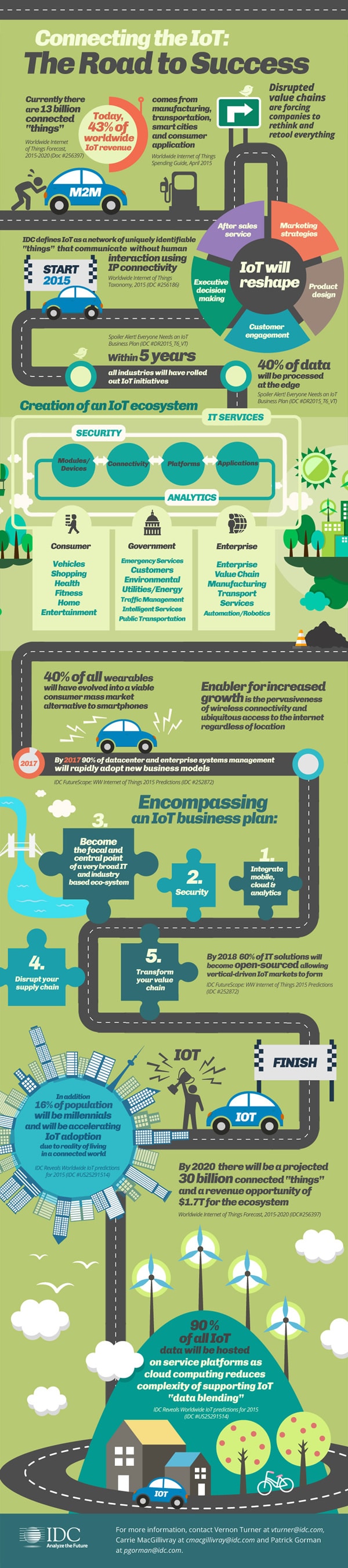
Finally, there is this somewhat older IDC infographic (2015) which might serve as a way to convince the board.
Looking beyond all the elements of the IoT ecosystem and the growth of IoT, the infographic has a piece on encompassing an IoT BUSINESS plan (let’s repeat that: BUSINESS plan). And yes, security is an intrinsic part of it.
As we wrote in the context of digital transformation success and failure reasons: don’t call in security when it’s too late. Involve them right from the very start. IoT projects are often deemed part of digital transformation projects and there is no reason NOT to involve security early on.
Top image: Shutterstock – Copyright: a-image – All other images are the property of their respective mentioned owners.


