The MITRE ATT&CK framework is a categorized and publicly accessible collection of adversarial tactics and techniques. The compilation has become a significant knowledge base and is used for various cybersecurity purposes.
Since the MITRE ATT&CK framework is based on real-life threat intelligence, it is, among others, used to improve organizations’ cybersecurity posture whereby one can take the position of the attacker.

By taking the perspective of the adversary across the framework (tactics, techniques, used language, etc.) the MITRE ATT&CK security model, corresponds more with a modern outside-in view as opposed to other models such as the CIA model that have a top-down and/or inside-out view, models with a focus on vulnerability scoring, and more. The framework, however, also looks at all aspects of an attack from the perspective of the ‘defender’ and more.
The MITRE ATT&CK tactics and (“why”) and techniques (“how”)
The ATT&CK framework stands for “Adversarial Tactics, Techniques, and Common Knowledge.” MITRE is developed by the American non-profit organization, the MITRE Corporation.
A critical use case for the MITRE ATT&CK framework is to gain insight into the attack techniques that an organization still needs to protect itself against or in what areas cybersecurity needs to be improved in order to be cyber resilient. One can also look at the methods and tactics in the framework that could be impacted by using a particular technology or making a specific change.
A cyberattack is typically a chain of events. As the MITRE video at the bottom nicely explains, MITRE’s ATT&CK framework describes how adversaries can penetrate networks and then, for instance, move laterally, escalate privileges, and generally evade your defenses.
MITRE ATT&CK looks at the problem from the adversary’s perspective. What goals do they want to achieve, and what specific methods do they use to get there?
To this end, ATT&CK organizes enemy behavior into a series of tactics, specific technical goals that an attacker wants to achieve.
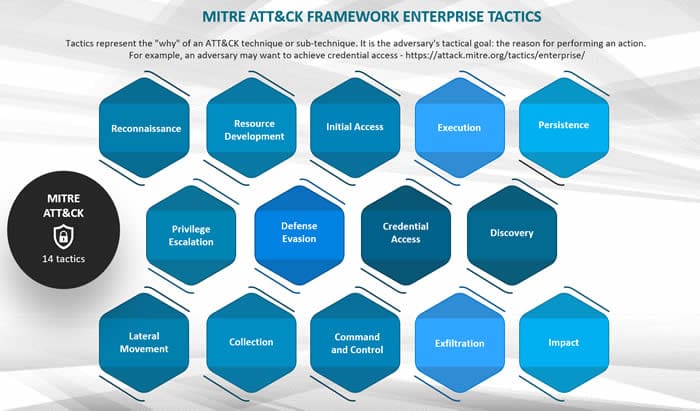
Examples of tactics are defense evasion (trying to be avoided to detected), lateral movement (trying to move through your environment), and exfiltration (trying to steal data). There are a total of 14 of these (enterprise) tactics. Each represents a different tactical goal of the adversary (the “why”) and consists of varying techniques and sub-techniques.
The illustration above shows each of the 14 tactics in the MITRE ATT&CK Matrix for Enterprise and a short description (source and more information).
ATT&CK defines this series of techniques whereby each technique describes one specific way an attacker attempts to achieve an objective (the “how”). Different techniques exist within each tactic because adversaries may use different methods based on their experience, their tools, and/or how your systems are configured.
Each technique for finding an attack includes a description of the method used by the adversary, the systems or platforms it covers, and, to the extent known, which adversary groups are using it.
Techniques also describe ways to mitigate the behavior and published references about the used technique. ATT&CK helps you understand how adversaries may operate so you can plan to detect or stop that behavior. Armed with this knowledge, you can better understand how an adversary prepares for attacks, launches them, and executes them.

