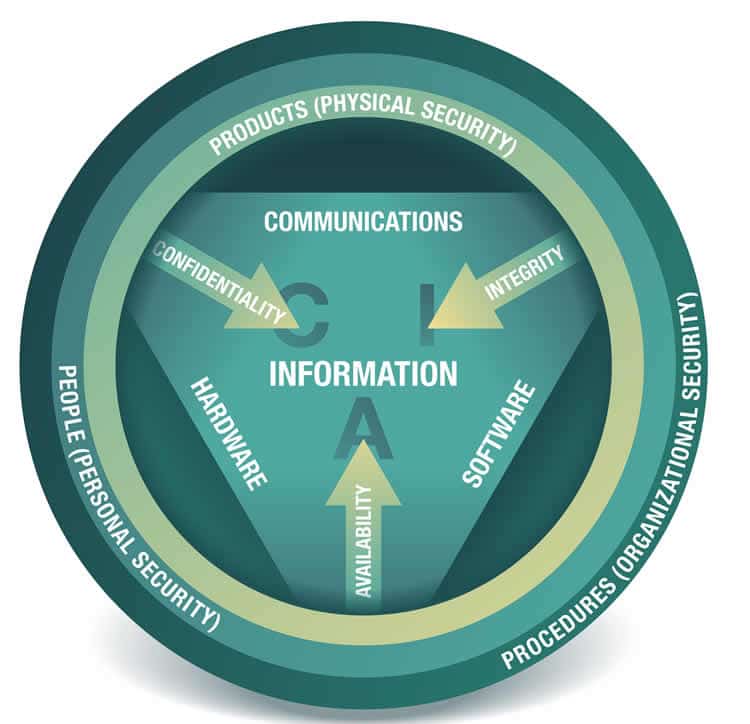
Confidentiality, integrity, and availability are known as the three essential goals, attributes, or qualities of information security, an essential part of cybersecurity.
You may also know the three terms as the CIA triad or CIA triangle whereby, of course, CIA does not stand for Central Intelligence Agency but – indeed – for Confidentiality, Integrity, and Availability.

The CIA security model has been around for several decades. The various elements have been discussed and emphasized in the context of information systems and information security, part of information management, since more or less the 1980s. The three elements of the CIA triad are so well known in information security and data security that countless definitions coined over the years for information security are built around the words confidentiality, integrity and availability.
We’ll look at some examples later, but it’s more important to know that we are also within the context of information security standards and cybersecurity models (and frameworks) with the CIA triad. Information security and cybersecurity are not the same (although often used interchangeably) but are closely related and overlap. Information security as part of information management and data security as part of data management also overlap.
Ensuring the confidentiality, integrity, and availability of information (security systems) is a fundamental goal of information security and cybersecurity and other domains, including privacy and personal data protection. The CIA model is therefore often seen as an essential cybersecurity model, and its elements are often also mentioned in the context of compliance.
Note, by the way, that the 2022 changes to the well-known information security standards ISO/IEC 27002 encompass various elements of cybersecurity – and, of course, privacy.
The essence of confidentiality, integrity and availability – CIA and cybersecurity
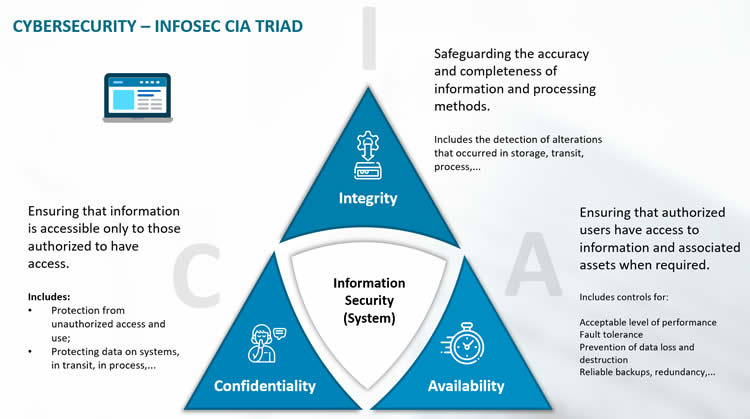
With the ISO/IEC 27002 standard, we arrive at one of those mentioned definitions of information security using the CIA information and security model terms, where each of the three words is further explained briefly. Per the standard, ‘information security is the preservation of’:
- Confidentiality: ensuring that information is accessible only to those authorized to have access,
- Integrity: safeguarding the accuracy and completeness of information and processing methods, and
- Availability: ensuring that authorized users have access to information and associated assets when required.
The various elements of the CIA model constitute a principle in information security. Of course, the model is not a complete representation of all aspects of information security. And even if information security and cybersecurity, in this era of digitalization and digital transformation, are increasingly close to each other, the CIA cybersecurity model misses aspects that are part of modern cybersecurity challenges. On the other hand, as mentioned, infosec standards are evolving.
Still, the letters of the CIA triad and especially their underlying meaning remain helpful in understanding information security, cybersecurity, and related domains. Moreover, they keep coming back. But they obviously do not constitute a cybersecurity framework.
Finally, note that there have also been several attempts to fill in the “missing” realities of information security and even cybersecurity in CIA with additional terms on top of the three known ones.
For example, in information standard ISO/IEC 27000:2009, where information security is defined as the preservation of confidentiality, integrity and availability of information, there is an additional note that “other properties, such as authenticity, accountability, non-repudiation and reliability can also be involved.”
In recent years, various authors have added goals/properties/attributes such as privacy, auditability, authenticity, utility, etc. Still, the triangle’s parts remain known and used as the primary goals for information security and, to an extent, cybersecurity in the information age. The CIA model has a more top-down view than the MITRE ATT&CK framework that is attacker-oriented.
Next: the CIA triad for cybersecurity.