Vishing or voice phishing is a method used by scammers to obtain credentials from victims. As the name indicates, the main difference between vishing and ‘classic’ phishing is the used medium to do so.
Whereas phishing traditionally relies on email, although social media and SMS (SMS phishing or smishing) are also firmly on the rise, vishing or voice phishing typically uses voice and thus the phone (typically voice over IP).

Vishing has been increasingly used in recent years, especially in more complex scams, attacks and data breaches. Vishing attacks are also forms of social engineering, often being part of hybrid phishing attacks. Usually, the attackers will pretend to work for an organization with some authority, such as a bank or government organization, with messages that strongly focus on a sense of urgency.
Targeted phishing campaigns that added phone calls (vishing or voice phishing) were three times more effective, netting a click from 53.2% of victims. (IBM X-Force Threat Intelligence Index 2022)
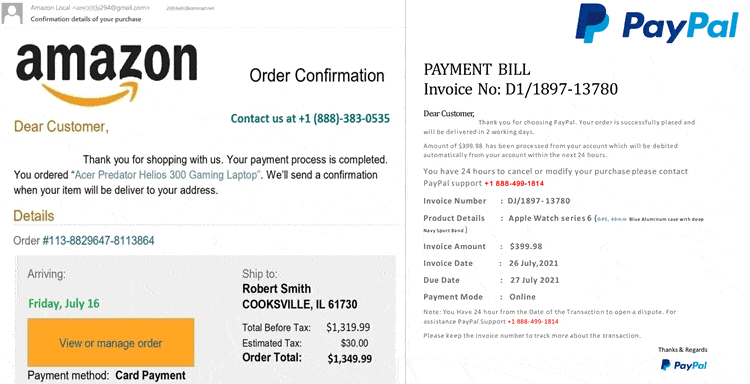
An example of a hybrid vishing scam is being sent a phishing mail with a phone number to contact a retailer about a large order you placed according to the mail (but never really did). Obviously, quite some people, when seeing such amounts in a mail that seems to be from a brand they know (and even by from), will panic and react, trying to avoid losing their money for an order they never placed. The emails often contain no links, so a call is an obvious action.
Other examples of vishing include incoming mails from reputable organizations such as your bank, a government institution (finance, IRS,…), a legal organization or a charity; you name it.
In a 2022 attack, a Cisco network hack occurred via an employee receiving vishing calls “under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication push notifications initiated by the attacker,” as is explained by Cisco in an excellent blog detailing the entire attack.
The evolution and effectiveness of vishing
Cybersecurity reports show relatively strong growth for vishing. And the reason is pretty simple: it’s a major cyber risk because it works and delivers for criminals using it.

According to IBM’s X-Force Threat Intelligence Index 2022, the click effectiveness for targeted phishing campaigns adding phone calls (vishing) is about three times more effective, netting a click from a whopping 53.2 percent of victims, compared to a click rate of 17.8 percent for the average targeted phishing campaign.
And according to Agari and PhishLabs, vishing cases increased almost 550 percent in the twelve months ending in Q1 2022.
Vishing attacks have even overtaken business email compromise (BEC) as the second most reported response-based email threat since Q3 2021 per Agari and PhishLabs. By the end of 2021, more than one in four of every reported response-based threat was a vishing attack, and this makeup continued through Q1 2022.
John LaCour, Principal Strategist at HelpSystems (owner of Agari and PhishLabs) added that hybrid vishing campaigns continue to generate stunning numbers, representing 26.1% of total share in volume in 2022 (the announcement was made in May).

