Chief information security officers (CISOs) and chief risk officers (CROs) don’t seem too worried about digital ecosystem partners, distribution partners, and the third parties in their supply chain despite the growing role of connected partners and ecosystems in cyberattacks.
Digital transformation is an ecosystem play – or, at the very least, an extended enterprise matter – and digital ecosystems often form the backbones in more mature stages of digitalization. Yet, additional cybersecurity risks have risen with the digital ecosystems of partners, suppliers, and competitors we’ve seen and still see popping up across industries or around specific digital business initiatives.
When asked to rank where companies will see the greatest number of cyberattacks between now and 2025, ecosystem partners came in last place (10th).
The role of connected partners, vendors/suppliers, supply chains, and a broad range of third parties isn’t new. However, the growth of risks and threats from an ever-broadening attack surface, with more partners and third parties than ever before, has been remarkable.

Interconnections in digital ecosystems as attack vectors
It’s a well-known fact that many cyber threats use the interconnections between our extended enterprises as attack vectors and that it’s increasingly more challenging for organizations to manage the associated risks and cybersecurity ‘trends.’
It’s why we see that increasing attention to third-party risk management in a cybersecurity risk context and for supply chain risks and even external attack surface management, as previously explained.
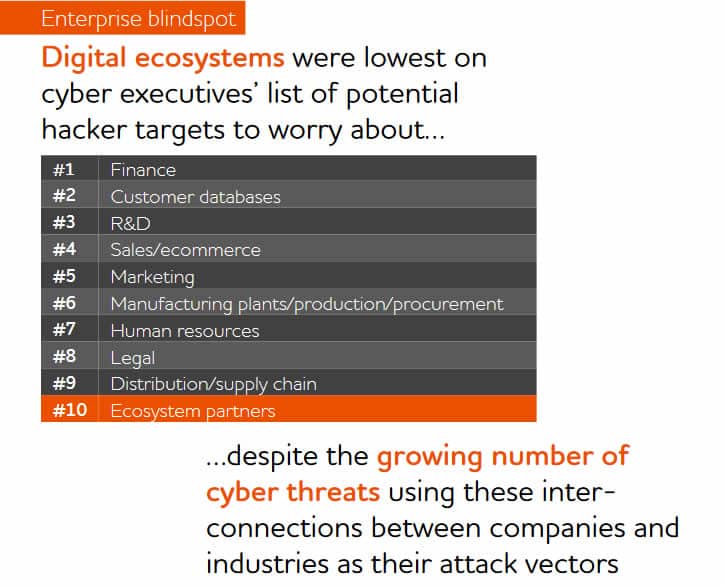
But as far as the threats from digital ecosystems are concerned, CISOs and CROs don’t seem too worried yet, as mentioned. In fact, according to TCS’ 2022 risk and cybersecurity survey of 600 cyber managers, ecosystem partners ranked last – in the tenth place – when respondents were asked where they expect the biggest cyber attacks between now and 2025.
TCS (Tata Consulting Services) concludes that cyber threats within digital ecosystems may be a blind spot for businesses. They are indeed, just as the cyber threats in our larger external attack surfaces and third-party networks are. In that regard, it’s also worth noting that distribution/supply chain ended in the ninth spot on the list of potential hacker targets respondents worry about.
Companies where the board of directors and C-suite are proactive about its cyber strategy are more likely to see better-than-average revenue and profit growth and fewer problems recruiting and retaining advanced cyber skills.
Ignoring threats from digital ecosystems: a blind spot that urgently needs to be addressed
Per TCS, at a time when companies are increasingly relying on digital ecosystems for their growth strategies, the survey shows that only 16 percent of Chief Risk Officers and Chief Information Officers identified digital ecosystems as a concern in assessing potential cyber targets. Only 14 percent of them cited the risks of these ecosystems as a top priority stemming from board-level discussions.
According to Santha Subramoni, Global Head, Cyber Security, TCS, ignoring threats from the digital ecosystems that organizations increasingly use represents a blind spot that urgently needs to be addressed.
You can check more findings from the TCS Risk & Cybersecurity Study here (PDF opens) and on the overview page.
Companies across the globe are increasingly turning to digital ecosystems of partners, vendors, and even competitors to reimagine and grow their business. Ignoring the threats originating from these ecosystems represents a blind spot which needs to be addressed urgently (Santha Subramoni, Global Head, Cybersecurity, TCS)

