SCADA systems and cybersecurity: it remains a challenge and according to ample research even one of the major restraining elements in SCADA market growth.
While being a multi-faceted challenge, one of the many means through which attackers infiltrate SCADA systems is the Human Machine Interface (HMI).
With HMI/SCADA software being in fully evolution in the age of Industry 4.0 and Industrial IoT, exploiting vulnerabilities in the software still happens a lot.
Security expert Trend Micro looked at the state of SCADA HMI vulnerabilities and had its Zero Day Initiative Team investigate all the publicly disclosed vulnerabilities with regards to SCADA software that were fixed from 2015 and 2016. The result: a report and recommendations. An overview and some additional thoughts.

The Hacker Machine Interface: focus on patching
The majority of found SCADA software vulnerabilities are preventable using secure development practices Trend Micro states.
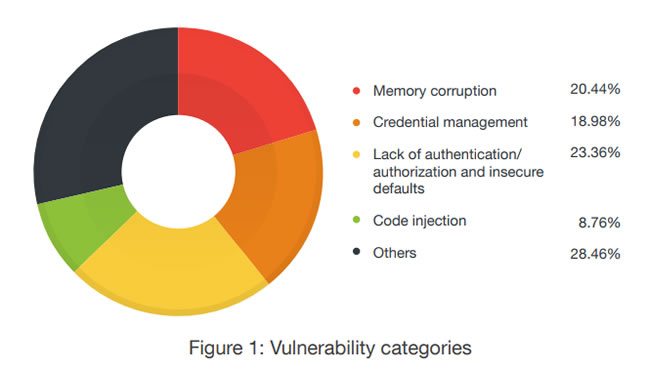
The major areas where SCADA software vulnerabilities occur as you can see in the graphic below are, respectively:
- Memory corruption.
- Credential management.
- Lack of authentication/authorization and insecure defaults.
- Code injection.
- A big chunk of other areas.
The press release, revealing the findings and serving as an announcement of the report “Hacker Machine Interface: The State of SCADA HMI Vulnerabilities”, also states that the average time it takes a SCADA/HMI vendor to release a patch once a bug has been disclosed can go up to 150 days.
Patching is a significant challenge for multiple reasons. The mentioned 150 days is approximately 30 days longer than it takes highly deployed software from the likes of Microsoft or Adobe, yet far less than enterprise applications from firms such as HPE or IBM, Trend Micro says.
However, knowing that SCADA systems are a bit everywhere and certainly in critical infrastructure, making them of course interesting for the ‘bad guys’ there is certainly room for improvement in the area of patching. As per usual we need to emphasize that 150 days is an average. So, when you’re in the market for HMI/SCADA software it might be a good idea to look at the security and patching practices of the various vendors out there.
Among the many concerns with regards to the security of SCADA systems, according to Trend Micro’s Fritz Sands the weak link really is the human machine interface software part and patching comes in again.
According to Sands most HMI systems still run on old Windows operating systems whereby there are no more security upgrades for the several versions of the Windows OS. Quoting Sands from a November 2017 article, entitled ‘Dated Windows software the weak link for SCADA systems‘, “Windows is a sphere where hackers feel very comfortable. Instead of needing a complex tool set to attack SCADA controllers, they have 20 years of hacking skills used against Windows, SQL server, browsers and Adobe products.”
Top SCADA/HMI security issues according to the Hacker Machine Interface report
On top of the fact that in the age of Industrial IoT everything is increasingly connected and we shifted away from the isolated HMI and SCADA system that runs on a trusted network whereby end-to-end security by design has simply become a must, as well as many other security issues (from the inevitable human factor and insider attacks to the traditional challenge of removable media and the ever more sophisticated ways hackers use beyond old tactics such as phishing and malware) solving the old Windows version security issue seems like a no-brainer. Certainly as the stakes, scale and indeed complexity of cybercrime expand.
Within the various SCADA solutions, the HMI represents the clearest and most present target for attackers. The HMI acts as a centralized hub for managing critical infrastructure. If an attacker succeeds in compromising the HMI, nearly anything can be done to the infrastructure itself, including causing physical damage to SCADA equipment. Even if attackers decide not to disrupt operations, they can still exploit the HMI to gather information about a system or disable alarms and notifications meant to alert operators of danger to SCADA equipment. (Trend Micro)
Back to the announcement of Trend Micro and some of the preventable SCADA/HMI issues the company found.
Below is an overview as mentioned in the announcement of the “Hacker Machine Interface: The State of SCADA HMI Vulnerabilities”. We added some quotes from the report which you can download in PDF here.
- Memory corruption problems, which account for about 20 percent of all identified vulnerabilities, mainly represent traditional code security issues with the likes of stack- and heap-based buffer overflows and out-of-bounds read/write vulnerabilities.
- Credential management challenges, accounting for a pretty impressive 19 percent of all vulnerabilities range from not protecting credentials enough and storing passwords in a recoverable format to the use of hard-coded passwords.
- The category of vulnerabilities in the area of lack of authentication/authorization and of insecure defaults accounts for close to a quarter of all found SCADA vulnerabilities (23 percent to be precise). One of the issues: missing encryption. Another one: unsafe ActiveX controls marked safe for scripting.
- The issues with regards to code injection are relatively minor in comparison with the others, accounting for 9 percent of all identified vulnerabilities. But of course, although perfect security is close to impossible, that is still far too much, certainly given the mission-critical role of SCADA and the fact that on top of the more common injection types there are also domain-specific injections as Trend Micro states.
Security strategies and security by design as the stakes get higher
Mentioning the crucial types of information such as a facility’s layout and critical thresholds SCADA system hackers can obtain (on top of the in the world of IoT not unknown phenomenon of getting device settings for future attacks) and threats such as the Stuxnet attack on an Iranian nuclear plant and Ukranian electrical grid attacks to provide an idea of the scope of potential damages, Trend Micro invites you to check out the various vulnerability types, cases of vulnerably SCADA Human Machine Interfaces and the much needed advice in its paper “Hacker Machine Interface: The State of SCADA HMI Vulnerabilities”.

By the way: needless to say that in times of ongoing digitization and digitalization, organized cybercrime, state-sponsored attacks and ‘cyber’ as a real weapon in warfare, industrial cybersecurity cannot be an afterthought.
Not in SCADA/HMI software, not in SCADA systems, not in industrial transformation, not in critical infrastructure, not in Industry 4.0 and not in digital transformation or IoT projects overall.
Security by design and security strategies need to be included from the very start of any project, not just because of the risks but also because of the fact that calling in your cybersecurity folks too late is a slowing factor in digital transformation to begin with and, the other way around, security is a digital transformation accelerator.
In a SCADA/HMI security context the call to do more in the words of Trend Micro’s ‘ The State of SCADA HMI Vulnerabilities: “despite the obvious risks of obtaining unauthorized access to critical systems, the industry behind the development of SCADA systems, specifically HMI vendors, tend to focus more on equipment manufacture and less on securing the software designed to control them”.
Top image: Shutterstock – Copyright: MOLPIX – All other images are the property of their respective mentioned owners.

