C-level executives are increasingly targeted by cyber criminals with financially-motivated social engineering attacks according to the Verizon 2019 Data Breach Investigations Report (DBIR).
Cybersecurity needs active management awareness, attention, buy-in and involvement. The consequences of attacks simply are too important, no digital transformation projects can succeed without it and on the level of personal data protection the stakes have become too high.
Fortunately, cybersecurity and cyber resilience are becoming a board-level issue – at least, so the Cybersecurity Trends 2019 report from TÜV Rheinland seemed to indicate. Yet, there is another reason for management to pay even more attention to security and especially to an area that concerns them. In fact, C-level executives are increasingly the targets of cyber crime. It’s one of the findings from the Verizon 2019 Data Breach Investigations Report (DBIR), the twelfth consecutive edition of the report.
According to the DBIR 2019, C-level executives have become the number one target for social engineering attacks (also think phishing) and are increasingly and proactively targeted by social breaches. This increase goes hand in hand with a rise of social engineering attacks with financial motivation. And, indeed, what better targets than the people who are closest to an organization’s most important and sensitive information?
Social engineering attacks with financial motivation and the C-suite
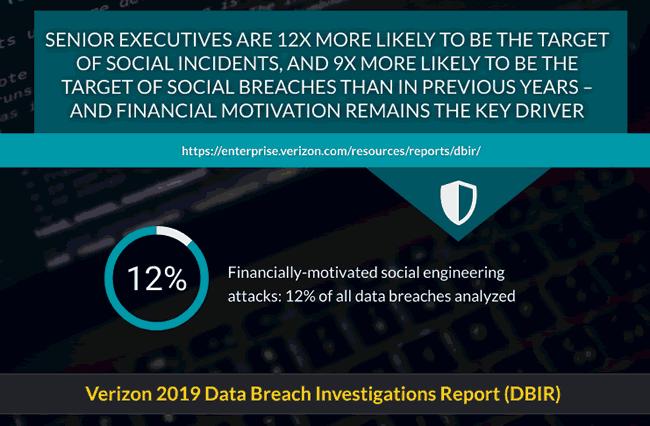
Financially-motivated social engineering attacks get special attention in 2019. The data show why: according to the DBIR, senior execs are nine times more likely to be the target of social breaches than in previous years and even twelve times as likely to be the target of social incidents – indeed with financial motivations remaining the key driver.
The aim of the focus of the Verizon 2019 Data Breach Investigations Report on the phenomenon aside from the growing numbers: emphasizing that all levels of employees need to be clearly aware about the potential consequences of a cyber crime. Since execs are so close to sensitive information we’d even say they especially might want to be aware of it.
A successful cyber attack on senior executives can reap large dividends because of their – often unchallenged – approval authority, and privileged access into critical systems, Verizon states.
According to the Verizon 2019 Data Breach Investigations Report senior executives are typically time-starved and under pressure to deliver and that increases the chance of suspicious mails getting true because they apparently tend to quickly review and click on emails prior to moving on to the next – or have assistants managing email on their behalf as Verizon says – in which case of course these assistants might need more awareness and education.
Verizon states that the increasing success of social attacks such as business email compromises (BECs -which represent 370 incidents or 248 confirmed breaches of those analyzed), can be linked to the unhealthy combination of a stressful business environment combined with a lack of focused education on the risks of cyber crime.
The executive summary of the report (PDF opens) further underlines the growth of financial social engineering attacks by stressing that both security incidents and data breaches which compromised executives rose from single digits to dozens in the Verizon 2019 Data Breach Investigations Report.

The dynamics of cyber crime: locations and targets change; tactics remain
Awareness and education remain important and all in all for staff there isn’t that much that changes with regards to the ways cyber criminals operate.
Although the different editions of the DBIR show changes in, for example, the targets with this year the attention for social engineering and C-suite executives, it’s important to keep in mind that in the end the tactics pretty much remain similar. In fact, 98% of security incidents and 88% of data breaches continue to occur within one of nine patterns.
In the words of Bryan Sartin, executive director of security professional services at Verizon: “Even though we see specific targets and attack locations change, ultimately the tactics used by the criminals remain the same. There is an urgent need for businesses – large and small – to put the security of their business and protection of customer data first. Often even basic security practices and common sense deter cybercrime”.
That indeed seems to make sense with the huge attention – and price – for data breaches where personal data are affected in times when there’s more attention for privacy and personal data overall. Think about the EU GDPR with its vast set of data subject rights, personal data breach notification duties and potential fines, to name a few elements. And it isn’t just about customer data alone of course.
The 2019 DBIR includes data from more contributors than in previous editions, for the first time also from the FBI Internet Crime Complaint Center (IC3) in the shape of impact data from business email compromise (BEC) and computer data breach (CDB) reports. The 12th edition of the report contains analysis of 41,686 security incidents, which includes 2,013 confirmed breaches from 86 countries.
You can get the full report and executive summary, highlighting other findings on top of the mentioned ones (such as a data breach overview per industry, data on threat actors, used tactics, attack targets, evolutions and the necessary recommendations) via the report’s main page.






